NOTE: Please read FAQ No. 5 before reading this FAQ No. 6. An awareness of the significant differences between GDPR-heightened requirements for Pseudonymisation and pre-GDPR “casual” uses of the term is a prerequisite to appreciating the benefits outlined below. Data Pseudonymisation 101 Overview Summary:
www.pseudonymisation.com Detailed Overview:
GDPR Recitals 78, 85, and 156 and Articles 6(4)(e), 25, 32, 40, 89 specifically recognise properly Pseudonymised data –
meeting new heightened standards of GDPR Article 4(5) – as an appropriate safeguard to help satisfy numerous GDPR requirements. GDPR-compliant “Pseudonymisation” is referenced fifteen (15) times in the GDPR, compared to “Encryption” which is referenced only four (4) times, and “Anonymisation” which is referenced only three (3) times. No other Privacy Enhancing Technique (PET)
1 is referenced in the GDPR.
The GDPR expressly awards certain benefits to the use of GDPR-compliant Pseudonymisation. These include, but are not limited to, the following:
- Tipping the balance in favour of the controller for Legitimate Interests processing (Articles 5(1)(a), 6(1)(f), and WP29 WP 217);
- Flexible change of purpose (Article 5(1)(b), WP29 WP 203);
- Expansive data minimisation (Articles 5(1)(c), 89(1));
- Flexible storage limitation (Articles 5(1)(e), 89(1));
- Enhanced security (Articles 5(1)(f), 32);
- Expansive further processing (Article 6(4), WP29 WP 217);
- Flexible profiling (WP29 WP 251 rev.01 - Annex 1, Recital 71, Article 22); and
- Ability to lawfully and ethically share, combine and enhance data (recitals 42 and 43, Articles 11(2), 12(2), EDPB WP259 rev.01).
A publication by the European Union Agency for Cybersecurity (ENISA),
Recommendations on Shaping Technology According to GDPR Provisions: An Overview on Data Pseudonymisation,2 also highlights the following benefits of GDPR-compliant pseudonymisation:
- Pseudonymisation serves as a vehicle to “relax” certain data controller obligations, including:
- Lawful repurposing (further processing) in compliance with purpose limitation principles;
- Archiving of data for statistical processing, public interest, scientific or historical research;
- Reduced notification obligations in the event of a data breach.
- Pseudonymisation supports a more favourable (broader) interpretation of data minimisation.
- Pseudonymisation goes beyond protecting “real-world personal identities” by protecting indirect identifiers.
- Pseudonymisation provides for unlinkability between data and personal identity, furthering the fundamental data protection principles of necessity and data minimisation.
- Pseudonymisation decouples privacy and accuracy, enabling Data Protection by Design and by Default while at the same time allowing data about individuals to remain more accurate.
While GDPR-compliant Pseudonymisation has many benefits, using it effectively requires significant expertise. The same ENISA report highlights that effective Pseudonymisation is highly context-dependent and requires a high level of competence to prevent attacks while maintaining data utility.
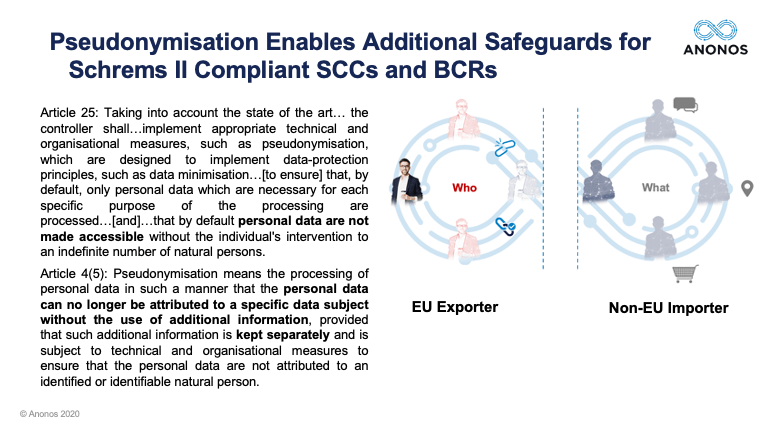
This means that for GDPR-compliant Pseudonymisation, the only way you can get back and forth between the gap between the “Who” data and the “What” data in the graphic above must be via access to additional information that is kept separately by the data controller. Therefore, by definition, if you can re-link to identity without access to this separately held additional information, it is not GDPR-compliant Pseudonymisation. Conversely, if a Non-EU Importer cannot re-link to the identity of data subjects without access to additional information that is held by the EU Exporter in the EU, it should satisfy Schrems II requirements for additional safeguards for lawful data transfer.
In summary, both the benefits from, and the technical and organisational requirements for,
3 achieving GDPR-compliant Pseudonymisation are significantly underappreciated. An example of successfully implementing GDPR-complaint Pseudonymisation to enable lawful data use under Schrems II is available at
https://www.anonos.com/variant-twin-value-proposition.
