
Gary LaFever (Anonos) - Moderator
 [00:00]
[00:00] Good morning and good afternoon. We welcome you to our second in a series of expert panel discussions about Schrems II additional safeguards. My name is Gary LaFever and I'm the General Counsel and CEO of Anonos, a global technology company specialising in GDPR-compliant Pseudonymisation and Data Protection by Design and by Default Technology and I will be serving as your moderator for today's event.
Again, our first webinar was three weeks ago today, on the 8th of October. At the time, we really didn't have plans for a second one. But we've had such a strong response that we were lucky enough to put this together and we're very pleased to present this expert panel.
The first panel actually focused and included NOYB’s Romain Robert as well as the EDPS’ (European Data Protection Supervisor) Anna Buchta. And due to scheduling conflicts, neither Romain or Anna were able to attend but there are a few people who could replace both of them and one of Gabriela. So, we are very happy to have Gabriela with us today.
I just want to talk about the level of interest in Schrems II additional safeguards dramatically increased over the last three weeks. From the questions and comments that we have received, it’s because companies are becoming aware how disruptive termination of data flows can be. Not penalising, termination.
I just want to give you a sense of who you are sharing this webinar with. In addition to our first class group of panelists today, there are 59 countries participating in today’s event; 1700 separate companies and firms; 41% of you are General Counsels or report directly to the General Counsel; 35% of you are privacy professionals - Chief Privacy Officers and Data Protection Officers; 22% are Outside Legal Counsel and Advisors; and 2% are Government Officials. When you look at the numbers and the level of seniority who are participating on this webinar, it’s really a testament to how important and critical these things are and how critical clarity is as to the availability and applicability of additional safeguards. Because again, the fact that the ruling in Schrems II was about stopping data flows and not just penalising is a big difference.

What I'd like to do very briefly since they are unable to join us is just highlight two quotes - one from Anna and one from Romain - from the last webinar. And the first one from Anna is that people should not fall into the trap, that the goal of additional safeguards and SCCs is to allow all the transfers that occurred prior to Schrems II. In fact, the truth of the matter is the fundamental rights that were the subject of Schrems II actually do require us to approach business differently and that is the healthy approach to doing it. But again, not at the cost of business, but rather business done correctly in compliance with and respecting and enforcing the fundamental rights of individuals. So, again, the goal of this webinar is to provide clarity on how you can continue your operations.
And from Romain, he pointed out that the three potential additional safeguards we will discuss today, which were initially raised by a German Data Protection Authority and have since been reiterated by both the EDPB and the EDPS. Romain brought the issue up that they are really not additional safeguards and that in fact you should be doing those already. Those three are encryption, Pseudonymisation, and anonymisation. And so, one of Romain’s points was if you are doing what you should be doing already correctly, it is less of a data transfer issue and more of an issue of “Are you within compliance?”

And I bring to your attention if you're not already aware that just last week, the EDPB finalised their opinion on Data Protection by Design and by Default. Data Protection by Design and by Default is just that by default you should be using just the minimally identifying data.
With that, I would like to provide each of the panelists an opportunity to introduce themselves. Gabriela, if you would please go first.

Gabriela Zanfir-Fortuna (Future of Privacy Forum)
[04:55] Hello everyone and thank you very much, Gary, for this introduction. My name is Gabriela Zanfir-Fortuna. I am a Senior Counsel for the Future of Privacy Forum, and I have experience in Brussels working for the European Data Protection Supervisor around 2013-2016, so just when the GDPR was being negotiated and the Privacy Shield as well. Prior to that, I wrote a thesis on data protection law particularly on the rights of the data subjects. So, I’m very much looking forward to our discussion today.

Gary LaFever (Anonos) - Moderator
[05:34] Thank you very much. Patrick?

Patrick Van Eecke (Cooley)
[05:37] Thank you, Gary. And thank you all for again being here and giving me the opportunity to discuss with you and the other panel members the impact of Schrems. I am a Lawyer and a Partner at Cooley. I'm heading the EU Privacy Department. I think it's indeed very interesting that we do a kind of follow-up webinar because it looks like things are distilling and crystallising, Gary. We see that more and more often that over the past few weeks and months some best practices are being developed, although not tested yet. We see some guidelines that are being issued by local authorities like Baden-Württemberg and the others. The advantage probably of being a lawyer based in Brussels that you can see and hear what's happening and what we recently heard was that the European Commission is going to come out even within two weeks to four weeks with a new set of standard contractual clauses, and they think about going to also to have to include some safeguards that we would need to encompass these kind of issues. So, happy to have that discussion with you guys.

Gary LaFever (Anonos) - Moderator
[06:51] Thank you very much, Patrick. And John?

John Bowman (Promontory)
[06:55] Hello. Good afternoon from London, UK. Good morning to those of you in the United States. It's a pleasure to be here again. Thanks, Gary, for inviting me back onto this illustrious panel. My background is I work for Promontory, which is a consulting firm. I work in the data protection and privacy practice. We advise lots of international clients on matters such as this today. So, cross border data transfers in particular. So, it's certainly a topical issue, as we all know. I was sort of hanging around Brussels around the time that Gabriela was there. I was the UK’s lead negotiator on GDPR between 2012 and 2014. And certainly, when the various articles relating to cross border data transfers were discussed, they sort of stirred some interesting and topical debate which sort of perpetuates to this day as well and we’re still trying to work it all out. So, events like this are good in trying to clarify our understanding of how the law applies and how it has evolved in respect to the judgments. So, I will leave it at that for now.

Gary LaFever (Anonos) - Moderator
[08:20] Fantastic! John, thank you for that. And Maggie, if you please introduce yourself.

Magali Feys (Anonos)
[08:26] Yes. Hello, I'm Magali (Maggie) Feys and I work as a Chief Strategist - Ethical Data Use for Anonos and I’m also an IP/IT and Data Protection Lawyer based in Brussels. We advise startups but we also assisted, for example, the nine different competence ministers of public health in drafting the legal framework of the digital and manual contact tracing in this COVID crisis. Next to that, I'm also writing a PhD on secondary use and purpose of health data. And with regard to the Schrems II decision, I'm honored to have been writing together with Gary the Data Embassy principles, which were submitted and apparently under active consideration by the EDPB. Thank you.

Gary LaFever (Anonos) - Moderator
[09:23] Thank you very much. So, as you see, we are very fortunate to have such an illustrious panel. But quite candidly, this panel is similarly impressed and appreciative of the quality of the audience for this webinar and the prior audience for the earlier webinar on October 8th. In fact, we've had so much interaction and so much vibrancy that a real community has developed within just a very brief period of time. And so, what we actually want to do before we start with the panelists is we want to start with you, the audience.
What I'd like to do is to walk through what we've created, which are the
5 Stages of Additional Safeguards under Schrems II. And yes, the graphics are meant to be a little comical, but it's because it's a very serious point and what we've done is we've gone through the questions, the comments, the interactions, and the phone calls that we've had with actual participants in the first and this webinar to create these. And these are available at
www.SchremsII.com/GetStarted. Before we actually start with a panelist perspective, we want to go into what we hear from you. I’m sorry. I forgot. Mark?

Mark Webber (Fieldfisher)
[10:45] Sure. Just briefly, I'm Mark Weber. I'm the US Managing Partner at Fieldfisher. I used to work and play my trade in London and in Europe and around six years ago I moved to the US where effectively I practice as a European Technology and Privacy Lawyer on the ground in Silicon Valley. I’m primarily working with technology vendors and cloud and SaaS providers, but definitely not exclusively. A number of those clients are clients themselves of other technology providers, of course, and we provide a holistic service around European privacy issues and technology generally to businesses who are expanding and doing business in Europe. We’ve been very, very embroiled in GDPR. During my time here, I was basically on the ground for the Schrems I decision, then for GDPR, and now for Schrems II and somewhat at the heart of data transfers and what's actually happening on the ground across the globe and speaking to a number of businesses, a number of regulators, and a number of interested parties as we all try to work out what this means to businesses globally.

Gary LaFever (Anonos) - Moderator
[12:11] Thank you, Mark, and I apologise for not previously introducing you. So, again, we have a great panel. But we want to first start off with what we’ve heard from you, the audience.

The first is Awareness. There is a stage before Awareness. It's called Denial. But if you were in the Denial stage, you wouldn't be on this webinar. So, for those of you on this webinar, you obviously are clearly aware of the ruling in July, and I think what we've heard from quite a few of you is initially you thought that the geographic location of the servers would be controlling and I think that's one of the things that has evolved and has been a little surprising to some, which is who owns the servers and not where they're located. And so, that’s the first stage - Awareness.
The second stage is Acceptance. And by Acceptance here, what we're hearing from a lot of different people is that there are different stages of maturity and understanding, but there have been a few additional measures noted. And so, as to those measures, how could they help? We spent a lot of time in the first webinar and we'll speak again about Data Protection by Design and by Default. And as I noted, just last week, the European Data Protection Board passed the final version of their guidance on Data Protection by Design and by Default. And so, the reality is you're supposed to be having certain safeguards in place, regardless of whether the data is being processed within the EU, outside of the EU, or in the EU but by companies owned by US or other nation companies. And so, that's Acceptance, which is: “Okay. The Privacy Shield is gone. I've made a decision that the standard contractual clause is the way I want to go. Now, what do I do with regard to additional measures and additional safeguards?”
Number three, at least again as we're looking through the interaction with the audience, is Understanding that at least at this point there are three that have been identified. No one of these will be a silver bullet, or a golden shield, or a magic wand. It will probably be a combination of these three and others that may develop over time. But these are the three that have been identified to date. And so, last webinar, we talked about the strengths and weaknesses of each of these. And I think what everyone came away with is it's likely a combination of the three that will work best and we'll touch upon the one which is Pseudonymisation in further detail because it's one of the FAQs that we're going to touch about. But this is not Pseudonymisation as defined prior to the GDPR. It's actually a heightened version with more stringent requirements. So, that's the third stage.

The fourth stage is the evaluation stage - looking at what your business objectives are, realising that some of what you did in the past will have to be localised and then other operations will have to be enabled by Data Protection by Design and By Default. How do you do all those things in a way that allows you to achieve your business goals?
And then, ultimately, I think everyone on this webinar is looking for that defensible business position. As noted by Anna Buchta in our prior webinar, this does not mean you do everything the way you did before without changes. Rather, you try to implement the minimal changes with the maximum benefit, respecting and enforcing the fundamental rights of EU data subjects while enabling you to achieve your business goals and objectives.

So, those are the five different positions. What we'd like to do now is to hear in real time from this audience as to where do you want your organisation to be. And I want to make a technical comment here, for those of you who are using a web browser, as opposed to the Zoom software on your computer, if you could please send just in the subject heading 1, 2, 3, 4 or 5 to
poll@SchremsII.com, we can count your vote as well. Right now, you should have on your screen those five options and we would love to see in real time where you would like your company to be - Awareness; Acceptance; Additional Safeguards - looking at what those are and learning about those; Evaluating those different options; or Do you want to be in a position where you have a Defensible Business Position?
We will take just a few minutes. Roughly half of you have voted already. So, the technology is working. It's always nice when that happens. We can always assume that that's the case.
All right. So, we're almost done with the voting. One more minute. I very much appreciate this. Rarely do you get the number of people involved at the level of seniority that we have for this webinar. Again, 1848 of you are registered, 59 countries. This is a great opportunity to both test what the panelists believe on these different issues and you yourself.
I believe we have the results. We're ending the polling now. And the results will show in one moment. If I had a drum roll, I would do it.
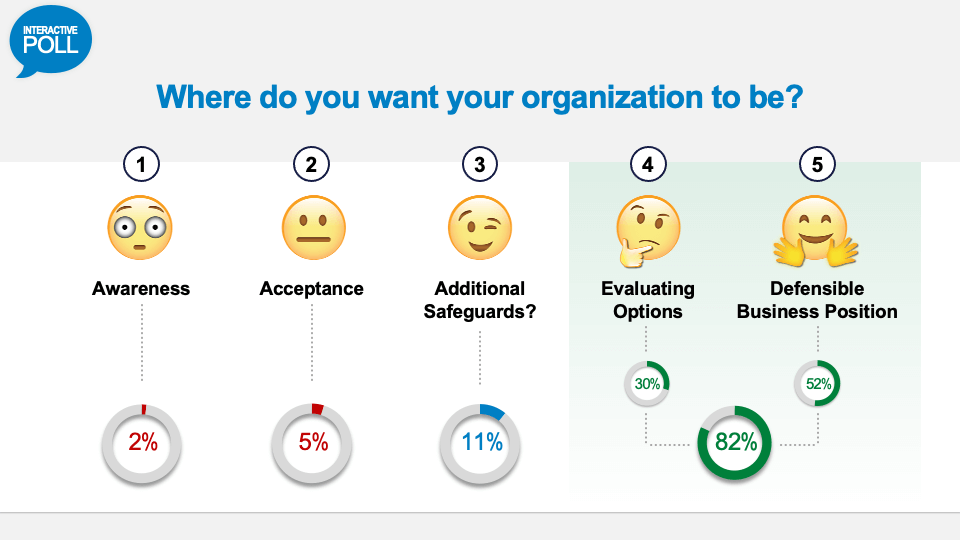
Alright, so fascinating here. This is where people want their company to be - Evaluating Options 30%, and Defensible Business Position 52%. So, I think that's very helpful and provides for the panelists a sense of where you are at. In that way, we are able to customise our presentations just a little bit and make it so that it's something that even makes more relevance to all those in the audience.
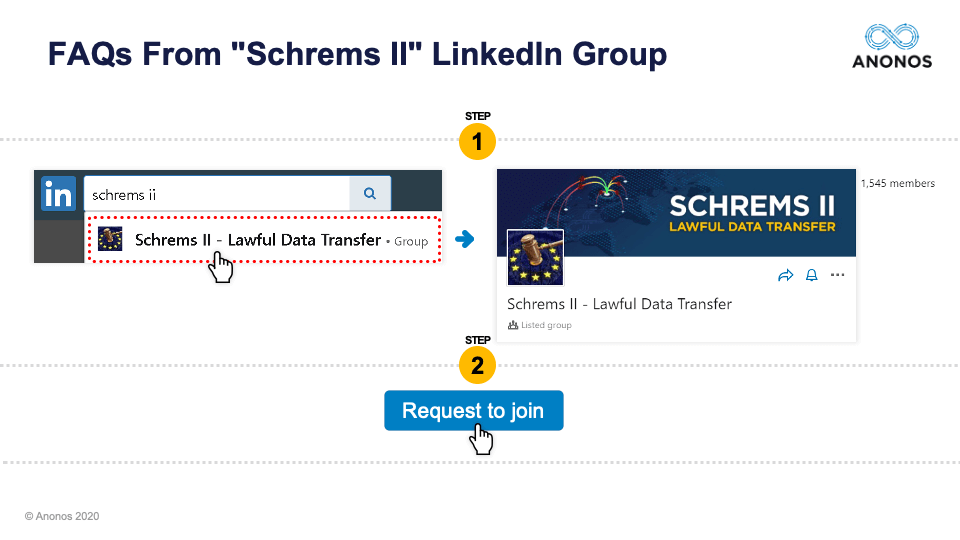
By the way, the way that this is going to be structured is we took the top five Frequently Asked Questions from the first webinar, and we will be answering those top five FAQs. But we are going to reorder them based on the interest level and questions that were raised by today's audience. But I'd like to ask everyone to do a favor right now before we do that. If you are on your browser, go to LinkedIn and search for “Schrems II - Lawful Data Transfer” and you will see the LinkedIn Group where you can read these five FAQs. I’m going to provide a very high-level overview of what those FAQs say, but this is where you can get the full text of those FAQs.
And so, what we'd like to do is to continue to keep this dialogue open and this community active that has been developed for very senior people who are looking for actionable ways to continue their business processes in compliance with Schrems II. And so again, if you would please go on to LinkedIn, just search for “Schrems II - Lawful Data Transfer” and then join.
For those that are interested, I also invite you to send out a personal LinkedIn invitation to me because I would welcome the opportunity to have a conversation with you directly. And I believe I speak for all the panelists as well that if you would like to speak and reach out to them directly, please do so. I would request that you join the group and also consider reaching out to myself and our other panelists so we can stay connected as things continue to evolve, as the European Commission comes out with new SCCs, as the European Data Protection Board comes out with the guidance, as the DPC in Ireland takes action with regard to the Schrems II enforcement. The ability to stay connected at a high level I think could be very beneficial for all of us.
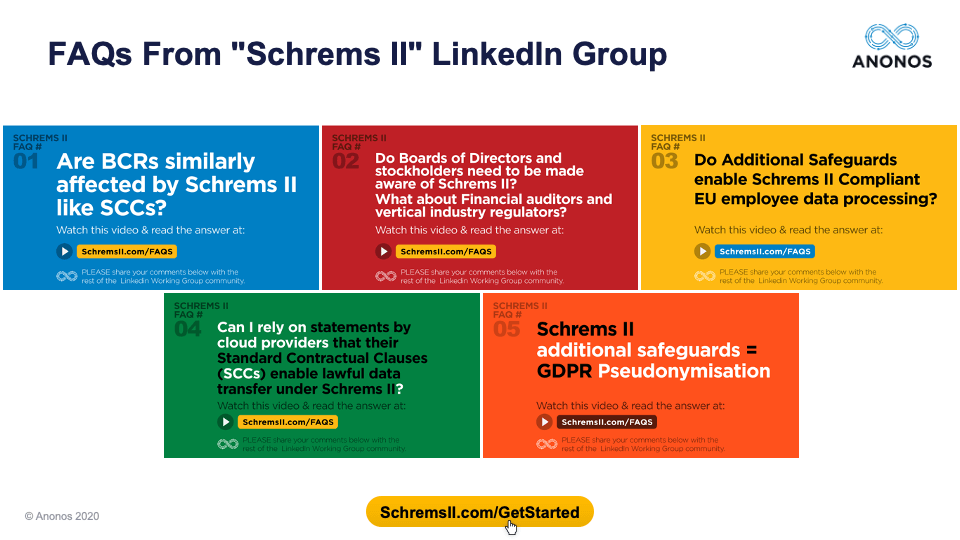
Alright, so we're going to move on to the five FAQs. And these are the five FAQs that we will be talking about today. Again, I will reorder them slightly and you can reach and review the original FAQs and the answers that were prepared by a group of lawyers, data scientists, and business people. But I do want to say that Maggie was a co-author, but the other panelists were not authors of these FAQs. So, we're inviting them to agree, disagree, embellish, etc.

Let’s proceed. The first one that we are going to address was actually the second Frequently Asked Question but it is by far the most often asked question in connection with this webinar -
Do Boards of Directors and Stockholders need to be made aware of Schrems II? What about financial auditors and vertical industry regulators? I'm just going to give you a high-level overview of what the answer to the FAQ was. Again, you can read those through the Working Group or at
www.SchremsII.com/faqs. One of the most prevalent questions that are being asked already for this webinar is your clients are asking for assurances regarding FISA and the Cloud Act. And the fact that clients are asking for that, does that raise that to a level of disclosure and a level of materiality? And of the things you’ll see in the LinkedIn Working Group is an article where Gartner predicts that by 2024, CEOs actually could be held personally liable for cyber breaches.
So, the issue here is that someone raised the term they thought that the GDPR had a 4% penalty, when in fact termination of data flows is almost equivalent to 100% penalty. Why is that said? Because without access to data, some companies can't even continue. So, is this relevant? Is this relevant enough that it actually becomes material and is it a disclosure issue for boards? And one of the things in the FAQ is an article in Financier Worldwide where it notes the increasing trend of Directors being held liable or the Board itself having culpability and also among stockholders. If there are publicly filed documents that investors make decisions on, does that obligate certain disclosures?
Also interesting, the International Ethics Standards Board for Accountants (IESBA) actually has a protocol called the Non-compliance with Laws and Regulations (NOCLAR), which obligates financial auditors to disclose to regulators if in fact there is material noncompliance. What’s interesting under NOCLAR is data protection laws are held at the same level as financial arbitrate as terrorism and as laundering of money. So, clearly, the International Ethics Standards Board for Accountants (IESBA) thought it was very important. Vertical industry regulators - what obligation do you do have to report to the European Central Bank, Bank of England, etc.?
So, this is a great topical question. Obviously, given the seniority of the people on this webinar, it's of a high level of importance. So, let's start with Mark, if we could get your perspective on whether or not this is a disclosure issue and reaches and achieves a level of materiality that requires this kind of action.

Mark Webber (Fieldfisher)
[24:09] Thank you, Gary. I think it is an issue that should be discussed at all levels within an organisation. And of course the Board and the Directors are not front face in all privacy issues but things should be trickling through to them. If you think about the GDPR generally, if you have a DPO appointed if you are an organisation, which triggers the requirements to appoint a DPO, that DPO has to have a reporting line up to and including the Board of Directors. So, I think these are the kind of issues that would filter through as a part of regulator reporting. A lot of mature organisations would have that kind of regular reporting in place filtering through to the Board level.
And then importantly, talking about what that defensible position is, I think it's really heartening to see that's the beginning of the feedback that we're seeing because we're all looking for a defensible position. Some people come from a position that transfers shouldn't be taking place at all. Others come from a position that these are critical to my business. So, you know, we're just looking to find the right solutions for the businesses out there and navigate those different views and the risks that are inherent with this CJEU decision.

Gary LaFever (Anonos) - Moderator
[25:32] Thank you very much, Mark. That was very well said. Patrick, please.

Patrick Van Eecke (Cooley)
[25:39] Sure. Well, I see exactly the same kind of evolution where I’m receiving client calls exactly on that topic. Do I need to make the Board aware? Do I need to make the Stockholders aware of these things? And yes, you have to, I believe, because when you're looking at risk exposure and this is what it is about, you always have to have that kind of calculation on the one hand the fine multiplied by the probability of “Is this going to happen?” And today, we know the fine. We know it's the highest fine you can get for data transfers. We have the 2% and the 4% fine calculation. Well, this and illegal data transfer falls in the basket of the 4% fine - the highest. So, that’s good to know because it means you can calculate as a company your potential liability exposure. Just doing the 4% multiplied by your global annual revenues, and that’s the worst case scenario.
Now then, looking at the probability that’s much more interesting because until now in Europe, we’ve got more than 300 fines already being issued throughout the European Union for GDPR infringements. However, to my knowledge, none of these refer to illegal data transfers. It’s one of those uncharted territories of the Data Protection Authorities. It’s all about not being transparent and no consent - the other types and the other kinds of rules of the GDPR. However, what we see now is that with the Schrems case, these things of course also come under the radar screen of the Data Protection Authorities and we also know that it’s the second time it’s under the radar screen because a few years ago with Safe Harbor we had the same issue and the same discussions. And what was interesting? Well, no Data Protection Authority fined organisations for data transfer and that’s exactly why None of Your Business (NOYB) just a few weeks ago has started claims against 101 companies throughout the European Union. They filed claims and complaints towards the Data Protection Authority about those 101 companies that are allegedly transferring data in an illegal way.
So, they're pushing it because they've learned from the Safe Harbor exercise that actually the DPAs were not doing anything and now the DPAs are going to be obliged to do something. So, that is probably going to trigger some actions from the Data Protection Authorities. So, if you are an auditor or if you have the responsibility within an organisation to calculate the probability of a sanction for an illegal data transfer (Yes, the fine. That’s clear.), now the probability from zero should probably be increased dramatically because of the fact that it’s now so much in the news.
And that brings me to maybe just a final topic on this, the Director's liability. For sure and certainly in Europe because I don't know about the Director’s liability in the United States, but the Director's liability in Europe is a hot topic and this kind of personal liability we see for GDPR infringements are similar to Director's liability, for example, for environmental infringements. And here, of course, today, it's going to be very, very difficult for a Director of a company to say: (1) “I didn't know about it.” Because you do know where the data are being transferred to. (2) “I didn't know that it was illegal.” Because it's all over the newspapers. (3) “I didn't know we had to do something.” This is not going to fly and that's also what Mark said, but we don't know yet what we have to do. It's not clear yet, but we know that we need to do something and that is of course something that we have to discuss here also during the webinar. What can we do to exactly have this kind of acceptable business kind of position? Not going too far, but going to be as far as possible to have an appropriate narrative towards the Data Protection Authority or towards potential customers or end users to say: “Yes, we've done our homework. We've done something. And yes, we are able to transfer data and we feel sufficiently comfortable to do that.”

Gary LaFever (Anonos) - Moderator
[30:13] Thank you very much, Patrick. Gabriela, I'd like you to go next and I'd like you to respond to the question that was posed that because based on this one person's interpretation of Schrems II that the directive to the DPAs was to enjoin to stop the data flows and not to punish and that therefore it was almost effectively a 100% penalty, not a 4% penalty. So, if you wouldn't mind just incorporating that in your response to overall this FAQ.

Gabriela Zanfir-Fortuna (Future of Privacy Forum)
[30:44] Yes. Absolutely, Gary. I would say when I saw the question, I thought: “Oh my! That’s the easiest question that one can ask around Schrems II because it has an absolutely immediate answer.” And that answer is an emphatic “yes”. Yes, you should bring this to the attention of the Board because it’s very relevant and you’ve heard Anna Buchta two weeks ago in the webinar saying that DPAs and Supervisors are looking at this as meaning a moment in time where things will start being different than they were before. And I would agree with this point, Gary, that these orders that DPAs can take can actually affect much more a company or a business than a fine.
To this point, I remember an older case from France about two years ago, a case from the CNIL, which was looking into the ad tech industry. The CNIL had opened about three or four cases. They actually issued orders for compliance and they gave these companies three months to bring their practices into compliance. These were French companies that were involving the mobile ad tech ecosystem. The entire Data Protection bubble was watching that and paying a lot of attention because it would have been one of the first cases with a fine against a company for ad tech practices or ad tech-related practices. But three months later, those companies actually managed to bring their processing in compliance but at least one of them with the representatives of which I had the opportunity to talk told me that: “We did not get any fine and it was great and there was no negative publicity that we were fined or anything like, that but we were actually ordered to erase our database that we had built over the past three or four years. And frankly, Gabriela, that was much more painful than a fine.”
So, yes, you might not see a fine. If you see a fine, that’s going to be super consequential because I am sure most of you are paying attention and you are seeing that whenever there is a fine issued by the DPA, you always see coverage in the media of that especially for the fines that are the first in a series of - for example, the first fine on international data transfers. That’s going to make headlines a lot. But then you also have the risk of actually not being fined but being on the receiving end of an order to erase data or to stop transfers.
This is one of the super big innovations of the GDPR compared to the former directive. The fact that Data Protection Authorities now have increased powers that includes this type of orders. And of course, there is an internal process and I agree with Mark and with Patrick to this extent that you need to pay attention to what you report to the highest level in your company, but this is a matter that they should be aware of for sure.

Gary LaFever (Anonos) - Moderator
[34:48] Very well said. Thank you, Gabriela. Maggie, if you could please give your perspective.

Magali Feys (Anonos)
[34:54] Yes, thank you. Well, first the short answer. Do the board of directors and need to be made aware? Of course, yes. Now, the longer answer. It's not that I disagree with Patrick or Mark. Not at all, but I think it's really what Gabriela said. Schrems II is, I think, unique because it obligates the Data Protection Authorities to stop unlawful data transfers rather than to impose penalties. And so, I think that the potential impact of terminated data flows can be naturally much more adverse to the operations of a company than only between brackets of fines. And we have already seen some Data Protection Authorities coming back with their opinions and asking to stop certain international data transfers whether it was with regard to medical or health data, whether it was with regard to the learning platforms that are used now in COVID times for the children that have to stay at home.
So, it can really have really big consequences not only from a responsibility or liability and penalty point of view. So, it should really be brought to the attention of the highest level in a company because additional safeguards have to be taken definitely when there is an international data transfer to the US. So, you have to think about those additional safeguards. But as I always say, when doing a GDPR exercise, please do not only think about the fines. Actually avoiding fines should be an additional advantage to get out of the exercise, but think of the GDPR exercise as doing it from a positive impact and creating or applying appropriate and additional safeguards will also have its benefits on the data security and keeping your company and the data flows secure, which I think in times where cyber attacks are only going up is very important, but it also can have really business goals with regard to secondary repurposing.
And so, it can really have its benefits. By applying these appropriate or additional safeguards, you have to start rethinking and we saw that in the answers. We are rethinking business models. We are rethinking processes. And then, that also is a company exercise. It’s as Mark and Patrick pointed out. It’s not only a legal exercise and it’s not only a technical exercise, but it’s really across the entire company that you have to do it. And of course at that point, management has to take it’s decisions in that. Taking actions for Schrems II should also not be a standalone action but it should be embedded in the entire GDPR exercise because I believe that when applying appropriate safeguards and we will come back to that, it’s like communicating vessels. It will also make sure that you actually comply with other requirements under the GDPR so it really has a lot of benefits.
I really want to emphasise that because I do know for big companies, of course, the fines are very important, but you can imagine that also, for example, working with innovative startups, they might say: “Oh, but we will not come at that directly in scope of the Data Protection Authorities.” And then, sometimes the argument of fines does not work also because it's a negative exercise, but then the benefits of applying additional safeguards, but really from management onwards is I think a much more valuable exercise. Thank you.

Gary LaFever (Anonos) - Moderator
[39:10] Thank you very much, Maggie. John, if you would please provide your perspective on this.

John Bowman (Promontory)
[39:16] Thank you. Well, I certainly agree with what all the previous panelists have said. Some excellent points made there. Just addressing the question. Do Board of Directors and Stockholders need to be aware of Schrems II? Well, I think if they lack awareness of data protection or GDPR in particular in general then that’s an issue. Schrems II is almost like a bit of an icing on the cake. But if they do already have awareness, then Schrems II is absolutely relevant. Most international organisations will consider themselves to be data-driven organisations. Data does flow from entity to entity and from country to country. And if the appropriate safeguards are not in place, either through the normal controller processor arrangements or through the international data transfer mechanisms, then they will be in violation of the GDPR.
In terms of what can happen, I think the regulatory enforcement regime now across various countries in Europe is starting to pick up pace. I think it has taken a little while to settle in, but I think we are going to see more and more cases start to come through the system as the regulators gain their feet and their perspective and start to think about where are the key issues, which arise in the context of data processing. And clearly, the case itself does raise huge issues in terms of international data transfers and the ability to effectively run a business. So, I think the point that Gabriela made, in particular, about the ability of regulators to suspend data flows or terminate them is a very powerful one and if those safeguards aren’t in place then it could be a sanction that they could enforce running alongside the administrative sanction regime now of course that individuals do have the right to judicial remedies as well.
So, if they feel that there has been a violation, they don’t necessarily have to go through the regulator routes. They could take it to the courts and see what happens there. And on top of that, certainly in the UK at least as I can't speak for other European countries, but there is Director liability related to criminal offenses, which can be committed under the UK Data Protection Act. So, Directors, Secretaries of companies, and offices of the companies can be held liable in the context of a criminal offense committed under the data protection legislation and that could include various things including the re-identification of de-identified information, without authorisation. That is a criminal offense. So, Directors certainly do need to be aware of that.
I mean, in terms of financial auditors and vertical industry regulators, I can't really speak for those regulators, but there are generally discussions which go across industry regulators. I always think of privacy and data protection as a matter of horizontal applications. So, you know, regardless of which vertical you're in, data protection, good data governance, all the things that you're supposed to do to comply with law cuts right across all data processing activities, and therefore pretty much every single activity that a company or an organisation undertakes. So, everyone needs to be aware of it. Data protection has horizontal effects. If the information is transferred across borders either for administrative purposes or commercial purposes, then this applies.
The other thing to bear in mind is that for companies that are service providers, regardless of whether they've been subject to a sanction, quite often their clients will do due diligence and they may well want to understand whether a company has been under investigation or even some sort of warning had been issued by regulators. So, that could effectively prevent them from getting a deal if it has been seen that there has been some sort of investigation with an outcome on the regulators for violation of the regulations. So, you know, sticking with the law is so important in every single way for a viable business in order to keep doing what they are to do. So, I'll leave it at that for now.

Gary LaFever (Anonos) - Moderator
 [44:10]
[44:10] And John, what I'd like to do is use that to actually segue to the next question. The Board of Director question barely beat out this one. This is one that a lot of people have asked. In fact, I'm going to combine several questions that were asked to put it nicely (and some of the questions were not put quite this nicely) that either the US big tech companies have not read the ruling and understood or they are purposely misleading their customers. These were some very pointed questions and statements that we have SCCs in place is only half the question because under the GDPR, it's a data controller obligation. It's not a data processor obligation. It's not a vendor obligation. And so, it's not that I'm defending anyone. But the reality is, my own personal view and obviously the panelists will disagree with me if they don't hold it is that it is imprudent for a data controller to expect any company to satisfy their obligations when under the GDPR they're clearly set forth as one of the data controllers.
And so within this answer to the FAQ, there's a copy of the Cloud Security Alliance (CSA) shared responsibility matrix, and it makes it very clear that information and data are always the responsibility of the data controller and not the data processor and not the vendor. And so, SCCs by themselves simply do not make transfers lawful. And so, this is I think a hot button topic here, which is whether or not technology companies that say that they have SCCs in place so don't worry are actually in good faith dealing with the issue because the data controller has a separate obligation to ensure that they comply. So, John, since you went last if you could please go first on this one. I appreciate it.

John Bowman (Promontory)
[46:15] Yeah. Well, I think the Schrems II ruling had some quite specific advice in terms of the obligations of the data exporter. So, this would be generally an EU data controller and the recipient organisation wherever they may be. So, the key thing that needs to be taken into account effectively are appropriate safeguards in place. Now, we know that the court did not dismiss standard contractual clauses. They survive to live another day and we know that there is work in progress with the European Commission to update the current set of clauses. So, in some ways, this is still a work in progress and I think all the parties of any sort of data transfer transaction will need to keep a close eye on the policy developments here. So, hopefully, a new set of standard contractual clauses will be available in the not too distant future and hopefully they will be able to answer some of these questions about how these standard contractual clauses provide appropriate safeguards.
Whether cloud providers have provided statements or not saying that they are lawful and that SCCs are fine, I don’t know the details on that. So, I wouldn’t want to speculate on where they’re coming from if they have said something like that. But I think really the whole ecosystem needs to be bought into this whether it’s the data exporter, the providers, the services providers, the vendors, the controllers, and the processors and sort of understand that ultimately the objective is to safeguard the data and effectively provide the actionable rights, which the court demands in the third country that the data are transferred to.
I think just one other element of this is what can the industry itself do to organise themselves and really sort of set a standard, which is acceptable to regulators. There is the ability under GDPR to make transfers based on the agreements of approved codes of conduct. So, if there is an industry code of conduct, which has been developed, then potentially that could form a basis for transfer, which is legal under GDPR. But I think we are still in a state of flux at the moment that there are considerations to be made with regards to the supplementary measures and the guidance that the EDPB will be issuing in due course and also the standard contractual clauses, which are under review at the moment.
So, I think I don't want to provide a definitive answer to that question in some ways because we are in a state of flux and I think maybe it's one that we can revisit in maybe six months’ time just to see what progress has been made. I think the terms of the Schrems II judgment were in some respects slightly unexpected and caught us all a bit off guard. So, we're all trying to absorb the real world application and the practical implications of it. So, to some extent, wait and see but at the same time try your best to put in the appropriate safeguards if you're exporting data and putting those measures when you do so.

Gary LaFever (Anonos) - Moderator
[50:16] Thank you, John. Gabriela, I would like to go to you next. And if I could, I'd like you to respond in addition to whatever else that you want to say to two things. The first is, I think it caught some people by surprise that international data transfers are not just data transferred over the Atlantic. That processing of data by cloud providers even if the servers are in the EU, if those cloud providers are owned by US companies both under FISA and the Cloud Act, they're subject to the restrictions of Schrems II. If you wouldn't mind, I'd love for you to comment on that, which is the cloud aspect and I'm combining cloud, Software as a Service, and outsourcing but it's the fact that if a directly or indirectly US-owned company or a company of any of the other non-equivalency countries, which is the vast majority of countries, is processing the data, is that an international data transfer? So, that's point one. Point two would be: I'm just going to ask you point blank if you agree with my opinion that no new SCCs from the European Commission will change the ruling under Schrems, that while SCCs are valid, they must be enforced by additional safeguards. And the reason I think that's an important question is people should not be waiting for new SCCs or even new guidance to start their process so they have a defensible business position. So, if you wouldn't mind, provide us your perspective.

Gabriela Zanfir-Fortuna (Future of Privacy Forum)
[51:48] Yes. Thank you so much, Gary, for this question. The question of what is a transfer and what falls under this ruling as well as under Chapter 5 of the GDPR is a question that I’ve been spending a lot of time thinking about and I think I would frame it a bit differently, Gary. It’s not necessarily an issue about who owns the business that has the server that’s located in Europe. Because from my point of view, that’s not really the criterion here. The criterion is whether there is any access to that server from outside of Europe. There are a lot of interpretations that push towards an answer to say: “No, that’s not a transfer.” And I heard my friend, Romain, also kind of saying the same theme. But based on my experience working on this for some years now and also based on something that the EDPB actually included in question 11 in their FAQ, the reality is that access from a third country constitutes a transfer of personal data. So, access from outside the European Union to data that is in the European Union constitutes access. And you know, there are many theoretical arguments that go to support that. But the easiest reference that I can make to give credibility to this interpretation is as I was mentioning an answer from question 11 in the EDPB FAQ because access would mean transfer as well.
Now to the question of how much someone can rely on statements by the big cloud providers, I would prefer not to comment on that because obviously we might don’t have access to all of the information that would be needed to provide an answer. But I would point out to controllers that are relying on cloud providers as processors that they should have entered into an Article 28 agreement with them - that’s a controller processor agreement - and one of the clauses in the Article 28 agreement must have referred to audits and inspections because that’s a requirement under the GDPR. And if you have a proper Article 28 agreement in place with them even if it was a template agreement, you do have that audit provision, which has obviously different shapes and forms. It can be a paper audit. It can be an audit that can be performed just once per year or I don’t know how that was shaped into those agreements, but you do have mechanisms to actually check and see whether what they claim is true.
Frankly, I think that these companies are very serious companies. But if you have questions, you do have the Article 28 controller processor agreement. One last pointer there, please check the latest draft guidelines from the EDBP on controllers and processors. It’s a very long document. I also still have to go through its entirety. But in those guidelines, you will also find useful pointers towards the control that a controller has and the mechanisms it has towards their processors and we are operating in what’s called a rule of law generally also in Europe and in the US. So, we have contracts that should be respected and if they are not respected, there are mechanisms to deal with that. So, that’s my intervention.

Gary LaFever (Anonos) - Moderator
[56:01] Thank you very much, Gabriella. Maggie, I would love for you to provide your perspective and specifically comment on something that Gabriela just mentioned there and one of the questions touched upon this that if 24/7support is being provided, chances are by definition that means someone has access outside of the EU. So, Maggie, if you would please provide your comments. Thank you.

Magali Feys (Anonos)
[56:29] Yes. Thank you, Gary. Well, yes, I do believe that the mere access as Gabriela pointed out I think was also indeed underlined by the EDPB that mere access is indeed a transfer of data or constitutes what is understood as a transfer of data under the GDPR. It's not to blame those cloud providers because I don't think that is what is the question is really about, but it is just to point out that of course by actually doing or providing some sort of services that even regardless of the location of the server being in Europe, that you are still actually falling under international transfer of data considered under the GDPR. And so, you fall under the Schrems decision. So, I think that is very important to take that into consideration.
And then, are the SCCs indeed enough? No, I think that is exactly the ruling of Schrems II where they said SCCs are valid. But next to that, you have to do it and that’s what was already touched upon in the other webinar is what some called data transfer impact assessment and you really have to see who has access or to whom you are transferring the data and see whether that country has an equivalent set of rules if it doesn’t have an adequacy finding and adequate set of rules in order to protect the rights of the data subjects. For example, it could be in some countries or with some data transfers SCCs could be enough because I don’t think Schrems II ruled that out but it’s stated and definitely with regard to the US that with the surveillance laws, they were definitely not enough and I know, Gary, that you pointed that.
I think from a theoretical point of view, Data Protection by Design and by Default is really an obligation imposed on data controllers. But as Gabriela correctly pointed out, you have to put in place under Article 28 these data processing agreements, and also Article 28 really imposes the affirmative obligation on data controllers to only use processes providing sufficient guarantees that they have implemented appropriate technical and organisational measures. So, you see, it might be then the burden upon the data controller. But once you sign the agreement and indeed sufficient data processing agreement should require from your data processor (for example, a cloud provider) to take additional actions and safeguards. So, if they haven’t done that, then at this point, the burden is as a company upon you.
So, I think that is really why it's important for controllers to really understand this decision. And I think for the cloud providers, this is really the moment and the opportunity because I also agree that just waiting on new SCCs they can bring some guidance, but I don't think they will be the Holy Grail or the silver bullets with regard to Schrems II because I don’t think they will be able, for example, to touch upon what is decent and appropriate judicial and administrative redress if your rights are being violated. And I think for cloud providers, it’s really now the time to think about Schrems II to find what appropriate measures you can actually provide to your customers and make it a unique selling point rather than waiting and sitting the storm out. Thank you.

Gary LaFever (Anonos) - Moderator
[01:01:02] So, Mark, I would love to get your perspective on this as someone who represents cloud providers. Again, the FAQ sets out that it's a shared responsibility paradigm and that the data controllers have certain obligations and certain obligations are on the part of the data processor or the vendor, but they have to be clearly set out. So, I would love to get your perspective on this.

Mark Webber (Fieldfisher)
[01:01:22] Yeah. Thanks, Gary. And I completely agree. SCCs aren't enough on their own, and there is joint responsibility and we knew that without Schrems II there is an obligation around transfers, which is either imposed contractually via Article 28, which the other panelists have talked well about or it sits there in the GDPR processors have to comply in respect of law transfers as well. So, what we’re really talking about here is something, which to go back to John’s point, is we are in a part of an evolving landscape right now and we don’t know what the right answer is. We can talk about what we think these additional safeguards are and what more needs to be done, but we are still getting to grips with what good looks like. In time, we will know what good looks like and we’ll be able to kind of move ahead.
So, clearly, you’re lumping cloud providers into one large bucket here and I know you’ve got the very large and some of which have not moved at all for lots. I think a number have done lots since Schrems II, and there is no doubt Schrems II is on the mind of the average cloud provider because that has been my life for the last two to three months. I think what we are talking about here is layers of protection, and I suspect we will come on to talk about this when we talk about Pseudonymisation and encryption and other safeguards. But where we are today is there are lots of ideas about what suitable additional safeguards may be, and there are some obvious lead runners. But as I mentioned in the last panel, the Schrems II decision and the EDPB advise, neither of them has actually come down and suggested exactly what those additional safeguards should be. I’m definitely an advocate of using as many safeguards as possible and layering them up and I think a number of us have talked to that already.
So, if you are signing SCCs, you’re already attaching them to an Article 28 agreement. That Article 28 agreement has the level of cover which needs to be put in place and it’s prescriptive about the kind of controls. Gabriela has mentioned the need to have inspections or audits depending on how you qualify them. We’ve talked about the other obligations coming out of Article 28. So, you’ve got that but you’ve got the SCCs themselves. Those SCCs themselves attach TOMs (Technical and Organisational Measures). You have to set out the security measures that are in place. Those security measures often already include levels of Pseudonymisation, levels of encryption, encryption at rest, encryption in transit. They can also be supplemented, and I think what a number of cloud providers are doing now and I would advise any cloud provider to be thinking about that is don’t start arguing about whether access is transfer. I believe it is. Start thinking about assessing the situation.
If we step back to what Schrems II asks us to do, we have to do that transfer assessment. We need to look at the risk data and what data is being transferred. Some of that goes back to our Data Protection by Default discussions from the last time and not necessarily transferring all the data. But then, having assessed the situation, we need to put in place SCCs if that’s the route we go and implement additional safeguards. Right now, I think some of the problem is someone out there just wants to run and put some kind of standard contractual clause in place and say “I’ve done it. Look I have a tick in the box.” Anyone who has ticked the box today and thinks they have closed off their transfer issue is wrong. So, what we’re trying to do when I’m negotiating deals is building some flexibility. We are looking at the ability to pivot and move to other transfer mechanisms. We might see a Privacy Shield 2.0. We might see, as John says, codes of practice and certifications coming out that might be a far better methodology. We almost certainly and we’ve all known seeing new standard contractual clauses, which will undoubtedly require other commitments. So, building in some flexibility into a deal so you can move that around.
Also, building in some ability to use the security measures and the Article 32 descriptions of your security to start addressing those additional protections that you're putting in place. And as any good security policy does, building in flexibility so that security can evolve. You know, we're talking about security, which has to be appropriate. What is appropriate today and offered by the average cloud security provider won't be what they're offering in a year. It might not be what they're offering in two months. These security process goals evolve, and the businesses are working on that. But I think you have to cut some of the cloud providers some slack. I work with businesses that have 70,000 to 80,000 customers on SCCs. You can't just rewrite all of them knowing that you are probably going to have to rewrite them in two months’ time. You're looking at doing things. I'm working on localisation projects, which will take a year. I'm working on end to end encryption projects, which will take six to eight months to implement.
The cloud providers are taking this incredibly seriously because to Gabriela’s and I think to Maggie's point, this gives competitive advantage. If you can show that you're on top of this and you have new techniques to offer and that you're reacting and you're able to articulate what Schrems II means and help your customers, you're going to be in a better position. And that's what a number of them are doing. The problem is as an individual user of those cloud services, sometimes you're a little stuck because you've already signed. Other times and I’ve seen it in the chat and I’ve seen a number of comments on your LinkedIn group that cloud providers won't negotiate. No, I understand. Many of them won’t, and many of the cloud providers themselves sit on other cloud providers and layered up, so they can't offer any more than they get off their primary host or from others.
So, there are some sort of changing of rules here and this will take time to flush out. This will take two or three years to flush out whether or not we stop data transfers, whether or not there are large fines or enforcements. I think there is a level to which we have to work with what we’ve got and put our best foot forward. But also realise that we just can’t fix it immediately. Yes, there are some that say: “We’ve got SCCs and that’s good.” Yes, you can challenge them if you can. Ultimately, as a customer, you can walk away. But I don’t think anyone wants that and I think what worries me the most about some of the debate and some of the commentary out there is Schrems has heightened our understanding around data transfers and it has talked about needing strong security, limited access to data, and that’s what we need to deliver.
I really don’t believe that anyone in the world is served by stopping data transfers and by inhibiting them. And as I said before, in the middle of a global pandemic when GDP is sort of falling off a cliff as it is, we don’t want to stop businesses trading. We want to find some kind of creativity, but that creativity is going to take time and everyone is going to feel uncomfortable whether you are a user of cloud services or a cloud services provider until we meet the position where we understand what good looks like and how we are going to move forward. And if we fill some of the vacuum that we’ve got at the moment, we won’t all be jumping because a regional regulator says something, some alliance says something else, someone proposes this, or heard a rumor about that. Everyone is reacting because there is no noise from the people that really count and that’s the EDPB. And I suspect we will see something from EDPB soon. Whether it will help us, I am not entirely sure but it will just take time for this to settle out and we need to work out how best to protect the data in context and not every solution is the same or every cloud provider is the same and not every transfer is the same. So, you actually assess what is being transferred, why, what you are doing with it, and how it’s potentially exposed and that’s the position you should start from.

Gary LaFever (Anonos) - Moderator
[01:10:14] Thank you, Mark. I just want to make all the panelists aware we have 45 minutes left. We've covered two of five of the FAQs. So, I would like to pick it up. And Patrick, unless you have something pressing that you want to mention on this, I actually would like to to move to the next one and have you start with that one. But just from my perspective kind of combining the answers that have already occurred, if in fact this is something that the board or the CEO or the C-suite needs to be aware of, if in fact this is something that won't be clarified for perhaps even a number of years, those two seem at odds. And so, I think the audience told us at the very beginning and we're going to do a re-polling after we're done with these FAQs and 82% of them wanted to be at either stage four or stage five. And so, I think the desire on the part of the companies to have a defensible market position makes a lot of sense.

So, with that, we're going to go to the next question. And this, we touched upon at length in the prior webinar and I don't think it's as much of a question as it was initially. And in fact, the EDPB was very clear in the FAQs. In fact, BCRs are similar to SCCs. So, I think hopefully we can make a quick coverage of this.
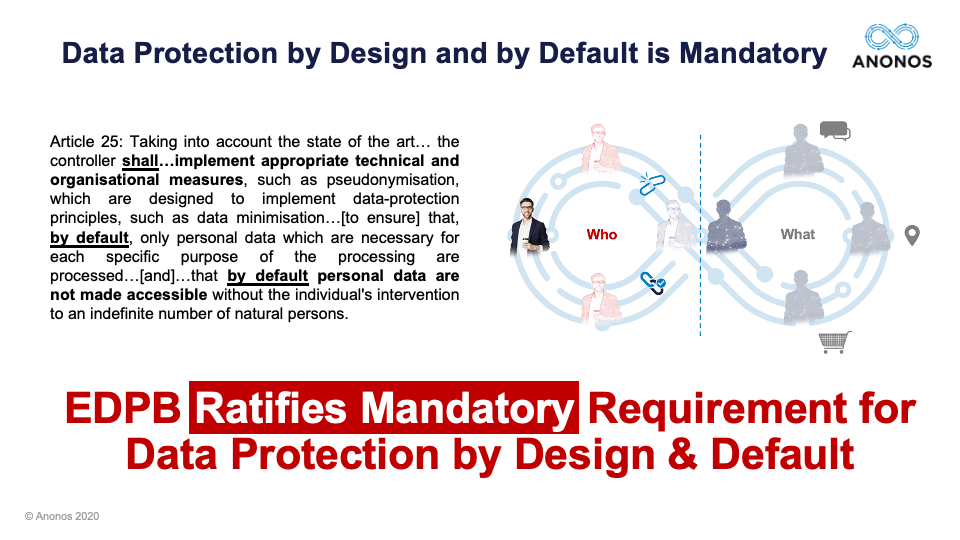
But I do want to mention again last week that the EDPB had mentioned that and ratified that Data Protection by Design by Default is not optional. It's mandatory. And at least working with our clients, those that are engaged in Data Protection by Design and By Default, complying with Schrems II is a lot easier, which is another way of saying perhaps the reason a lot of companies have issues with Schrems II is because they weren't already doing Data Protection by Design and by Default. So, if we could kind of pick up the response a little bit here. Patrick, if you would please go first. Thank you.

Patrick Van Eecke (Cooley)
[01:12:12] Thank you. I am with you and I was so well prepared to answer that question on standard contractual clauses. So now, I need to shift my mind to BCRs but I’m very happy to respond to this question because it’s a topic which is very close to my heart. BCRs, are they affected by Schrems II just like standard contractual clauses? And yes, they are. That’s very clear. Gary, you just mentioned that as well. So, the European Data Protection Board even stated explicitly that you also need to look into BCRs in order to make sure that you can have an appropriate data transfer. Yes, they are impacted but it doesn’t mean they are invalidated and that is a very important point I want to make. I even believe that BCRs for certain circumstances namely intra-company data transfers that they are the solution to the issue.
Not every company is going to go for BCRs, etc. But at least the companies that are currently having BCRs, I do believe that they could still remain valid in the sense that typically the discussion is going on about standard contractual clauses. It is typically because most companies just adopted and they just copy-pasted the standard contractual clauses and they never added additional kinds of clauses for the simple reason it wasn’t necessary. You couldn’t even deviate from standard contractual clauses because otherwise they were not pre-endorsed any longer. But what do we see with BCRs? At least, the BCR projects I’ve been involved in is a very thorough thinking process. It’s not just about downloading a set of standard contractual clauses from the European Commission's website, filling out the form and then signing it, and the next morning you’ve got data transfer legitimation. No, with BCRs, it’s a project where you really go in depth into the data processing activities and the compliance efforts of the company.
And very often what you notice, because you have that kind of relationship and conversations with the Data Protection Authority and the lead supervisory authority because you need to have an endorsement from what at least from the lead supervisory authority, it means you have this kind of discussions going on where the DPA already is guiding you and actually asking you before Schrems II to have this kind of additional safeguards in place. So, very often with BCRs, you see appendages about encryption and about Pseudonymisation. You see things about accountability, about transparency, and all these kinds of things. So, actually what it means to me is that as a company if you’ve got BCRs, the first thing you need to do now is to read them again. Probably nobody has read them since they were signed off, but you should take them back. You should ready them and check to what extent these BCRs would pass your kind of test of being a responsible data transfer or data importing company right now and exporting company.
It is very well possible that you may have to fine-tune the BCRs a little bit. Now, the good thing about BCRs is you do not necessarily have to go back to the Data Protection Authority to get an authorisation. It’s just a reporting obligation. I don’t want to go too much into the details. But if it’s a minor kind of change, you just put it in your annual report the BCRs to the DPA. If it’s much more kind of a major kind of add-on, which I can imagine some cases would be, you need to immediately report it. But the good thing is it’s a reporting obligation and it’s not asking for an authorisation. So, that would certainly be my first thing to companies having BCRs to go through them, read them, and do an assessment whether or not you already have this kind of beefed up BCRs that would stand the kind of test.
Other organisations that are currently looking to find a solution for this whole kind of debacle, I would say I would highly recommend to look into the opportunity of BCRs because many other companies are doing it. It's a lot about what others are doing. It's a lot about peer pressure. It's a lot about, as mentioned I think by Mark, getting competitive advantage. BCRs is one of those things, which certainly also adds to your competitive advantage as a company. But again, it's just for intra-company data transfers.

Gary LaFever (Anonos) - Moderator
[01:16:51] Right. And even there, I believe the EDBP made it clear that even BCRs would need additional safeguards, at least they would have to be evaluated.
So, in order to ensure that we can finish, I am going to move on to the next FAQ. And the reason this is highly relevant is that many people will cite an EU employee processing as an example of something that simply is impossible to do in compliance with Schrems II. The FAQ, which I won't go into a lot of detail, although it's a very detailed response, actually provides three different examples of how data could be processed by implementing and embracing Data Protection by Design and by Default. In fact, our experience, as I've said in the past, is companies that are following Data Protection by Design and by Default methodology have a much easier time of complying with Schrems II. So, again, we will use this question, but I would please ask each of the panelists to keep their responses to 30 seconds so we can complete it all. So, Mark, if you would please start.

Mark Webber (Fieldfisher)
[01:17:52] Yeah. I can say very briefly I think employee data is personal data. Personal data is regulated by the GDPR. So, you are applying very similar positions. I think when we get too focused on data transfers, we can forget that the GDPR puts in a number of other obligations and whatever you're doing as a controller with data, you need to be processing it fairly and lawfully. So, you need to be establishing the grounds for processing that employee data in the first place. And there are challenges with consent. You are more likely to be looking at legitimate interest processing or contractual necessity for these limited resources and even statutory obligation for certain types of reporting. So, you need to establish that.
Then, you need to look at the transfer and how you are doing the transfer. Employee data can be transferred subject to BCRs and subject to the SCCs, but you're looking at the same kind of things. You are doing a transfer impact assessment. And then, you are looking at the nature of the data, what is at risk, how it might be at risk, and then what additional safeguards can be put in place on top of that to protect the data. So, yes, you might have more sensitive data. Yes, you might make some different decisions, but you also need to be careful because not all employee processing is the same. You could be dealing with a controller to processor transfer. I suggest that's relatively rare in an employee scenario. A lot of the times the parent company in India or the parent company in the US will be using the data for its own purposes in determining the manner in which that data was used. So, you’re actually moving yourself into a world of controller to controller transfers, and then using a different set of data transfer agreement. There are two sets of SCCs available maybe for the next couple of weeks in relation to that kind of controller to controller transfer.
So, you know, a little bit more uncertainty about what the core expectations are and what EDPB expectations are in relation to those controller to controller transfers. I would suggest there's not a lot of difference that you need to apply the same kind of rules, and I suspect others in the panel will have views on that. But I don't think it's prohibited. You need to be careful. You need to also work out whether it's actually necessary. There's a lot of general replication of databases I find when actually not all that data needs to move in the first place. But yeah, context is king and there is more to deal with. Patrick's and others in Europe will be well aware of work councils and other approvals that might be needed, and you need to be thinking about other kinds of sanctions and permissions that you get from workers generally. But yeah, I think much the same kind of process with a little bit more due care and process because you may have that sensitive data.

Gary LaFever (Anonos) - Moderator
[01:20:46] Thank you, Mark. John? And again, if we could please keep these responses brief. I appreciate it, John.

John Bowman (Promontory)
[01:20:50] Yeah. Of course, yes. Well, again, I agree with everything that Mark said. Although there might be some outsourcing maybe to business process outsources for administrative purposes like pensions management and so on. But as Mark said, context is king. As a data controller, you should always understand what your data flows are and what agreements and arrangements that you have in place to transfer the data and what the recipient regime is like. As Mark did suggest, certainly for EU-based controllers, the handling of employee data often has its own sort of specific requirements, works councils, for example. In more so, the sensitive industries maybe financial services, which may be vulnerable to fraud, or those kinds of industries where there might be measures in place where you know there is sort of a data leak prevention.
There might be employee monitoring and that kind of thing. These have to be handled extremely carefully and sometimes these have to be done in arrangement with organisations like work councils as well. The employers really have to understand their legal bases in which they are able to undertake those particular activities. Now, if things like fraud prevention or some kind of potential crime prevention monitoring is taking place and that information is transferred outside of the jurisdiction, then I think there is a high degree of sensitivity around that type of information. And of course, maybe you'd have to make some sort of assessment that if there is a recipient in another country, whether national authorities may well take some sort of interest in some of that information as well. So, that's when you start to think about your supplementary measures and appropriate safeguards. So, I think just to conclude, employee data processing brings its own challenges and its own requirements and own considerations, and they should be considered in around both in terms of the controller processing and any information, which is transferred to third party or even to another entity of the same organization that is located in a third country.

Gary LaFever (Anonos) - Moderator
[01:23:21] Thank you for that. Maggie? And again, let's keep our responses brief. Maggie, please.

Magali Feys (Anonos)
[01:23:25] Yes. So, first I want to start with the bold statements that I believe that with Schrems II the writing was on the wall. And so, there was nothing really surprising. And as Gary already touched upon, people or companies that already implemented Data Protection by Design and by Default have a better job because I think with regard to international data transfer, that is exactly. It’s a little bit too bold and maybe too short but it’s what we really have to start thinking or we had already thought about the fact that also with relation to international data transfer that Data Protection by Design and by Default should be embedded in the way we thought about that. And so, I believe that essentially, any EU employee related data processing that can be done in a multi-step Data Protection by Design and by Default manner can be completed using Schrems II compliant Pseudonymisation. Thank you.

Gary LaFever (Anonos) - Moderator
[01:24:31] Thank you very much, Maggie. Gabriela?

Gabriela Zanfir-Fortuna (Future of Privacy Forum)
[01:24:34] Well, obviously, transfers of employee data are covered by Chapter 5 of the GDPR. But good luck there, I would say. The fortuitous thing with these transfers is that you do have a direct relationship with your employees and I would say it’s much easier to argue that your transfers are not massive even though they might be repetitive, so you are in a better position to use one of the derogations under Article 49 for sure. And then, of course, to the extent you can bring additional safeguards to that, the processing and the transfer lawfulness would be certainly supported if you want to go the route of relying on one of the derogations. I think the other panelists have already covered the option to rely on SCCs and on BCRs for that purpose. So, I will not refer to that.

Gary LaFever (Anonos) - Moderator
[01:25:50] Thank you, Gabriela. And Patrick, if you could please close this one up for us? No comment. All right.
Well, I think that enables us to then move on to the next question and that has to do with Pseudonymisation. Again, we touched upon this at great length in the prior webinar, but the only guidance out there so far is from regional DPAs and they have mentioned encryption, Pseudonymization, and anonymisation. And so, I encourage anyone who is participating in this webinar and did not see the first one, I'm happy to give you a link. We have a summary, we have a transcript, we have the video. But briefly though, I'd just like to summarize that Pseudonymisation (and this is something quite candidly I've learned in the last few months) - you have to be careful with this term. There were actually efforts during the drafting of the GDPR to introduce Pseudonymisation as a third category. So, you have personal data, non-personal data, and Pseudonymisation.
But those efforts were largely around trying to have looser requirements for Pseudonymisation. When in fact, as Anna Buchta made it very clear in the prior webinar, Pseudonymisation as approved and as reflected in Article 4(5) is a heightened obligation. So, as the panelists talk about Pseudonymisation, I would just caution the audience that they are not talking about loose tokenisation or pseudonymisation of only direct identifiers. They are talking about a very heightened standard, and I think that's very important.
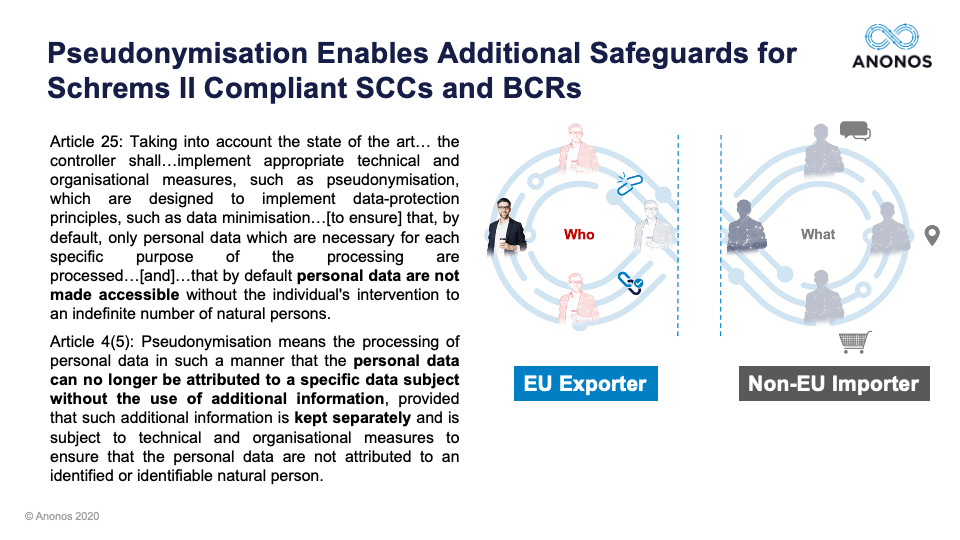
And one of the reasons I at least believe it's very important is because almost by definition, the Article 4(5) definition of Pseudonymisation literally says: “You must, on a result basis, be able to put controls in place so that an EU data exporter is the only one who can relink to identity.” And if in fact that that's been done, if the EU data exporter is the only one that holds the keys and the data is being processed by a non-EU importer, again, if you have in fact satisfied the definition of requirements, you should be in compliance with Schrems II. But with that, I'd like to start off and get the panelists’ perspective. Maggie, if you would, please.

Magali Feys (Anonos)
[01:28:04] Yes, of course. Thank you, Gary. So, yes, I also believe that GDPR has now given a new and higher standard to Pseudonymisation so it’s not applying a token. It’s not only a pseudonym. It’s also (not because I see that with a lot of clients) removing or deleting or encrypting the direct identifiers. But if you go and read the definition, it is really coming to a data set that without the additional information you cannot attribute that data set to a data subject. So, meaning that not only based on direct identifiers, but also indirect identifiers. And actually, you create a data set that could be called local anonymised data. And then, I just want to refer to my tap analogy of the last webinar where, of course, Pseudonymisation gives you higher data uses because anonymised data would only give you three drops of water. But with Pseudonymisation, you have the controls in place, which for example with international data transfer, you could keep with the EU data controller, but gives you still the controls in place to then open up the tap and give you the amount of water necessary.
So, I think it is very important for people to understand the concept and it’s no longer a technique but really a concept under GDPR that it’s not just failed anonymisation or taking away the direct identifiers but that it goes beyond that. And if you then take that heightened level of Pseudonymisation, then you will see why we take it as really a central element in the Data Embassy principles, which I already said we submitted to the European Data Protection Board because as an outcome, it really enables data minimisation under Article 5 and it is the establishment and the enforcing of Data Protection by Design and by Default techniques, which restrict processing to a form of personal data that does not enable the identification of the data subjects and that once again also gives you the benefits under Article 11(2) and 12(2). Whether you keep that additional information for the relinking only in the EU, you also have lesser obligations with regard to the data subjects’ rights because you already protected them by applying this Data Protection by Design and by Default concept. So, that’s why we really believe and it’s a key element of the Data Embassy principles but it is of course very important to then understand that we took the heightened new level of GDPR-compliant Pseudonymisation when you read those Data Embassy principles. Thank you.

Gary LaFever (Anonos) - Moderator
[01:31:32] Thank you, Maggie. Mark, I would love to get your perspective on this one.

Mark Webber (Fieldfisher)
[01:31:35] Yeah. I mean, it may just be worth it for the audience to just take a step back because we were really talking about Schrems II and this focus on national security access to data. And of course, Schrems II was really decided on the fact that potentially national security government states might be getting access to that personal data and then denying the individuals and their underlying rights in respect to that data because either they don't know it's been accessed or they can't then access their right to deletion restriction, etc., etc. So, we're looking at methodologies within our Schrems II analysis to reduce or limit access to that data. And yeah, that's why we talk about minimisation and Data Protection by Design and by Default principles to minimize that access. Because essentially if we've got strong security, we are limiting that potential access. The stronger that security, the harder it is to get that access, and the more likely we can justify the transfer of that data outside of the European Economic Area. So, that's what we are looking to do.
Now, Maggie has really well-described Pseudonymisation is one of those security measures. It's a technique which effectively stops an individual being attributed to certain data. It also preserves use of that data because it is unique in its own special way. So, it maintains some of the characteristics of a personal data once it has been transferred. Your diagram on screen right now shows it is no longer the Who and it's some of the What. So, it is a powerful technique and I agree there is an enhanced definition. In some ways, I think whether it’s an enhanced definition or not, I’m not sure it matters too much because I think many really haven't come across Pseudonymisation. I mean, we could barely say it before the GDPR. It’s a difficult word. So, I think many are looking at it afresh. It isn't part of a vernacular that many are starting to consider, but it is one of those additional safeguards, which can be applied alongside things like encryption and minimisation. I think this is where as a technical measure it’s fantastic if you compliment that with contractual organisation and policy measures and it begins to perform a set and a suite of safeguards, which can adequately protect that data when it’s transferred and then you’re doing your own risk assessment to work out whether it is powerful enough in those circumstances and that’s what we are really talking about here.

Gary LaFever (Anonos) - Moderator
[01:34:36] Fantastic. Thank you. And John, if you could please give us your perspective.

John Bowman (Promontory)
[01:34:42] Yes. Well, again, I do agree with colleagues here. It is a powerful measure which can be applied. It doesn't solve all your problems in one go, but I think certainly in the context of Schrems II, it can be applied as a measure alongside the contractual measures that you have in place and plus the risk assessments that you have done. So, any sort of transfer, which is potentially subject to Schrems II so anything out of the EU to a non-adequate third country should be taken in the context of the risk assessment and the measures both contractual and technical, which are applied. It was interesting that you mentioned that Pseudonymisation came up during the GDPR negotiations. I remember being approached about having it as a legal basis in its own right. So, the mere fact that you had the data being subject Pseudonymisation in itself would provide a legal basis and I think maybe that was considered to be a step too far.
But certainly, in terms of the utility of data and gaining benefit from data, it did make its way into the GDPR in Article 6(4), which effectively meant that it could be one of the measures which you could apply in order to do further processing without necessarily gaining the consent of the individual alongside a whole range of other considerations, which needs to be taken into account. So, I think the GDPR does call out Pseudonymisation in various parts of the text and clearly sees it as a way of providing some sort of privacy-enhancing measure. So, I think that’s my view on the topic generally. But as always, this needs to be taken into context of the information that you are transferring, the type of information that it is, and the safeguards that you put in place as part of the toolkit, which is available to data exporters.

Gary LaFever (Anonos) - Moderator
[01:37:08] And so, I'd like Patrick to go next. But before he does, I want to provide what may be my most significant contribution to this webinar. And that's how I remember how to pronounce Pseudonymisation. Because Mark made a good point. Most of us did not know how to say it. And do you spell it with an S or a Z? It's very complicated. But literally, I always think of if I'm standing at the head of an auditorium and I have two friends that just walked in. Sue comes in that door and Don comes in that one. It's Pseudonymisation because I have been corrected. Pseudo-anonymisation is not Pseudonymisation. Pseudo-anonymisation means anonymisation doesn't work. And as Maggie said, Pseudonymisation has been newly defined. And I actually want to put up on the screen for those who are interested,
www.ENISAGuidelines.com. The European cybersecurity agency actually has come out with two separate reports in November of 2018 and November of 2019. They go into a great detail about what is required to satisfy the requirements for Pseudonymisation under the GDPR. They have over 50 tests that they apply. So, I just put that out there as a resource for those on the call who want more information on what Pseudonymisation does mean under the GDPR. But with that, Patrick, please.

Patrick Van Eecke (Cooley)
[01:38:32] Thanks, Gary. And now I don't dare to pronounce that word any longer. But maybe just some background information, in Belgium, we actually have already Pseudonymisation legislation for about 25 years and I must apologise or maybe not because it's an opportunity for many of us, it actually went into the GDPR. But in Belgium, we had the Data Protection Directive transposed into Belgian legislation and also a few other countries it's in something similar. So, having this kind of pseudonymous data as a kind of intermediary between anonymous data and personal data and the only difference and that’s where the GDPR didn’t go that far is that under the former Belgian Law, Pseudonymisation could only be done by an intermediary by a kind of trusted third party. And so, you as a hospital, for example, you would be sending your personal data to the intermediary, they would actually pseudonymise it, and then send it further to the relevant recipients.
And so, the Pseudonymisation key if you can call it like that, would stay with a trusted third party and I do believe this is something we should keep in mind again. And certainly, you may have seen about the Data Governance Act that the leaked version of the European Commission that that they are going to propose on the 11th of November is again having some kind of reflection of using intermediaries to deal with personal data. We should keep that in mind that the European Commision is continuing to think about these kinds of efforts. Now, talking about Pseudonymisation in the Schrems II context, I don’t think and I think everybody agrees that this is the one and only solution. I don’t think it’s going to be sufficient. I don’t think it’s always necessary. But for sure, it is a great instrument in many different scenarios. And even I would take it one step further and that is to challenge the European Commission on pseudonymous data and could it become anonymous data if the Pseudonymisation key stays in European territory and you then send or transfer that pseudonymous data to the United States. But actually, what you are doing is you are sending pseudonymous data without a key so surveillance authorities would never have access to the key on European territory.
So, that could mean we could qualify those data or the pseudonymous data on European territory and it could become anonymous data and even Chapter 5 of the GDPR on data transfers would not be applicable because it’s only applicable to anonymous data, and this is a discussion. I do believe it’s a discussion that should be taken, that should be done, that should be undertaken. It’s a discussion between the distinction between contextual anonymisation and absolute anonymisation. And there, I do believe that the GDPR I'm explicitly referring now to Recital 26 of the GDPR, which is different than the former Data Protection Directive Recitals and the idea of what is anonymous data and what's personal data. I do believe that that Recital 26 about reasonably likely means to be used to identify an individual using objective factors, such as costs and time needed, that kind of formulation should go into the discussion whether or not pseudonymous data being sent to the United States or any other country without sharing the key could actually be considered as anonymous data. It could be a solution for the Schrems II issue because, as Mark already mentioned, at the end it all boils down to are you able to prevent foreign surveillance authorities to have access to personal data in clear and that actually would be prevented.

Gary LaFever (Anonos) - Moderator
[01:42:37] Patrick, very well said. And I want to reinforce something that Patrick has said. Nothing that we are describing during this webinar is meant as a silver bullet, a golden shield, or a magic wand. This is a very complex area. But what we did set out to do and hopefully we are in the process of doing it is share actionable issues with regard to what additional safeguards could be. And the only three that have been mentioned, albeit by regional regulators, have been encryption, Pseudonymisation, and anonymisation. And the other interesting thing and I would love Gabriela for you to speak on this is anonymisation if satisfied takes data outside of the GDPR. Pseudonymisation has, as one would argue and I would argue, even heightened standards because the Article 4(5) definition does not have a reasonableness standard. It says you cannot relink but for access to the additional information held by the data controller.
So, the interesting idea that Patrick just raised is might Data Protection Authorities be more comfortable in that scenario where pseudonymised data is provided for processing in the US so that it is not susceptible to surveillance, but it doesn't leave the jurisdiction of the GDPR so that if the Pseudonymisation process was done incorrectly, data subjects would have rights of recourse within the EU. So, again, the difference I'm focusing on is by making something anonymous, it's no longer subject to the GDPR. Pseudonymous remains subject to the GDPR. So, might that make it more likely that people would embrace it? Because if I send data to a US processor, which could be a US cloud or a SaaS provider with servers in Germany or France, if I'm not doing my job correctly as a data controller, my data subjects have recourses against me and the EU because it's still under the jurisdiction of the GDPR. So, Gabriela, please.

Gabriela Zanfir-Fortuna (Future of Privacy Forum)
[01:44:32] Thank you, Gary. So, absolutely anonymising personal data, but very importantly, when you meet the anonymisation standard of the GDPR and for that for the time being let’s say your most relevant resource is an older guidelines document from the Article 29 Working Party on anonymisation. If you meet that standard which is very high, then indeed the data processing falls outside of the GDPR. So, none of the accountability rules of any of the other rules and the principles of lawfulness and fairness and so on apply to the anonymised data set. It’s true that as regard to Pseudonymisation you have a very clear procedure in the GDPR but I would like to emphasise one of the points that Patrick mentioned that Pseudonymisation was not part of the former Directive. It was not addressed by the Directive. In Directive 95, you only had a black and white type of situation of personal data or anonymous data, which fell outside of the Directive.
The GDPR introduced Pseudonymisation specifically as a measure that decreases the risk of personal data processing with regard to data subjects. So, very clearly, pseudonymised personal data is personal data still. The GDPR indeed still applies to that data, which means that the transfers rules apply to that data as well. But there is also a recital in the GDPR Recital 28 that really spells out what the purpose of Pseudonymisation is, and that is the fact that the application of Pseudonymisation to personal data can reduce the risks to the data subjects concerned and help controllers and processors to meet their data protection obligations. So, it's definitely a measure that supports compliance, decreases risks to the rights of the data subjects, absolutely a measure that should be taken into account. However, I wouldn't dare to say what DPAs will think of Pseudonymisation in practice as the additional or one of the additional measures to SCCs for transfers, but I think the principle absolutely is that Pseudonymisation decreases risks to the rights of individuals and supports controllers to comply with their data protection obligations.

Gary LaFever (Anonos) - Moderator
[01:47:34] Thank you very much. Very helpful.

So, what we'd like to do at this point in time is we'd actually like to re-poll the audience. Having listened to this discussion by the panelists, previously 82% of the audience wanted to be in stage four or five - Evaluating Options or Defensible Business Positions. You've heard a lot of things said that some of these things will not be resolved perhaps for years. Yet, at the same time, it’s an issue of potential risk that needs to be raised to the C-Suite, to the CEO, and to the Board. And so, just curious and we will now take the poll as to whether or not people’s attitudes have changed. And so, we are asking you where you would like to be in these five positions - just awareness, acceptance, additional safeguards where you are aware of what at least has been discussed today, evaluating your different options, or in a position where you actually have a defensible business position. So, if you would please go forward with that. As I’ve said in the past, if you are using a web-based browser, you can send in the subject heading 1, 2, 3, 4, or 5 to
poll@schremsII.com and we will share that with you.
I want to mention as an example of why we encourage you to join the LinkedIn Working Group. While we have been having this webinar, the European Data Protection Supervisor has published
Strategy for Union institutions, offices, bodies and agencies to comply with the ‘Schrems II’ Ruling. So, that literally came out during the term of this webinar. And within the next 24 hours, we will include a post in the LinkedIn working group, and we would love to have everybody comment on that. So, please be sure to join the working group because it's a way for us to continue this community and this discussion as we go forward. And so, we will post an assessment of that on the working group, and we look forward to everyone's comments on that.
We're going to be leaving the poll open for another 30 seconds. So, if you have not voted, please do. We will be trying our best to stop within the hour. We may go a few minutes over, but we actually still have some interesting information to cover. So, for those of you who are still with us, please do not leave. And so, as we go forward, we will now have the results of this poll. Drum roll, please. I really should have had someone on the drums here.
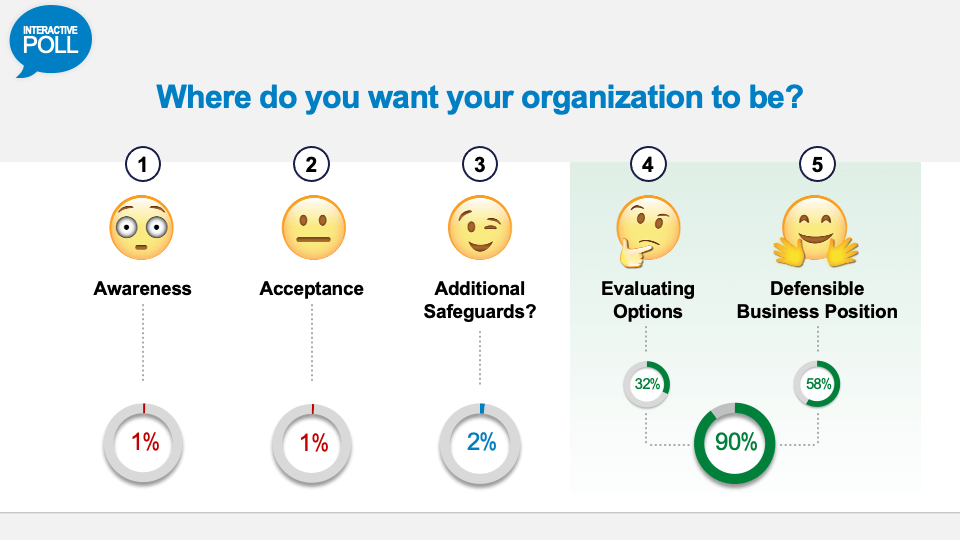
And as they're displayed. So, we are at 90%. So, it looks like a slightly larger percentage now want to actually ensure that they are in a defensible business position or evaluating options. And it is interesting. I always find it interesting to watch what EU member states do. So, if you look, the UK has announced revisiting their cloud-first strategy. In France, the CNIL actually went so far as to say that the data hub should be pulled out of Azure. But then, another French Court came in and said that may be the appropriate resolution but let’s look at this in a guided and guarded manner. And so, the EU member states are telegraphing the importance of this issue and one that needs to be resolved and that’s why just waiting is not really an option and rather taking position and actions are what is required but in a reasonable way as we’ve talked through during this.
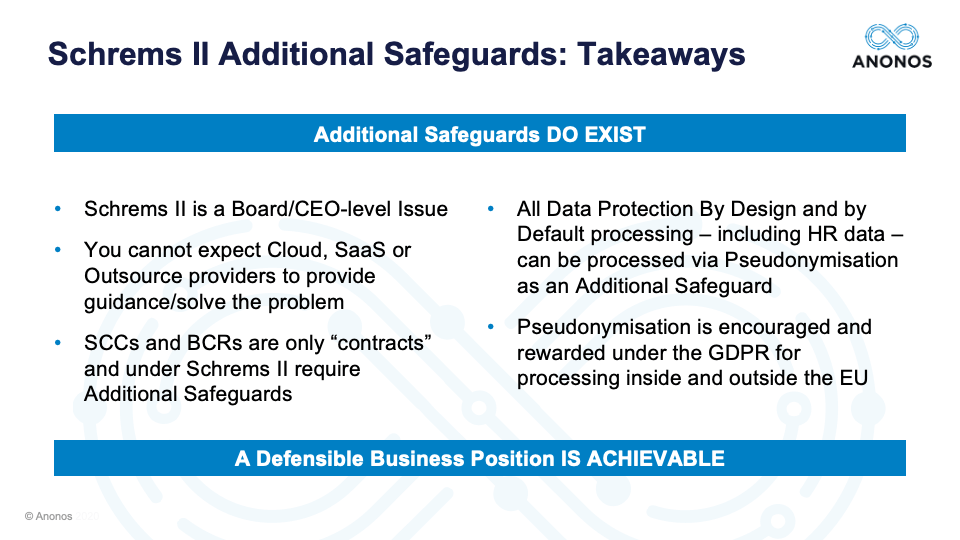
So, if I can summarise very quickly at least what I believe has been discussed today. First, Schrems II is in fact a Board/CEO level issue but it needs to work its way through the appropriate safeguards and structures and communications, but it is something that could have an impact and therefore needs to be considered. You really can’t expect cloud, SaaS, or outsource providers to provide you guidance to solve the problem. It’s a contractual issue and you should look at the contracts that you have in place regarding who is responsible for what. SCCs and BCRs both work, and Patrick made a very good case for BCRs that may work in more situations than they’re even currently being used for, but they are only contracts and one of the holdings of the Schrems II decision was in fact that contracts by themselves may not be enough. And when you are transferring to a country that does not have equivalent protection, you will need something more than just contracts.
Data Protection by Design and by Default - we have talked about it quite often but it’s actually mandatory whether you are processing data within the EU or outside of the EU whether it’s primary or secondary processing. And so, for companies that have embraced Data Protection by Design and by Default as just ratified by the EDPB as being required actually have an easier time of complying with Schrems II. Pseudonymisation is encouraged. It’s not a magic wand. It’s not a silver bullet, but it is a heightened standard that may be helpful as part of your solution and approach to Schrems II compliance. So, additional safeguards do exist. Greater clarity will be forthcoming and it’s clear that the majority of participants in this webinar want to achieve that defensible position.
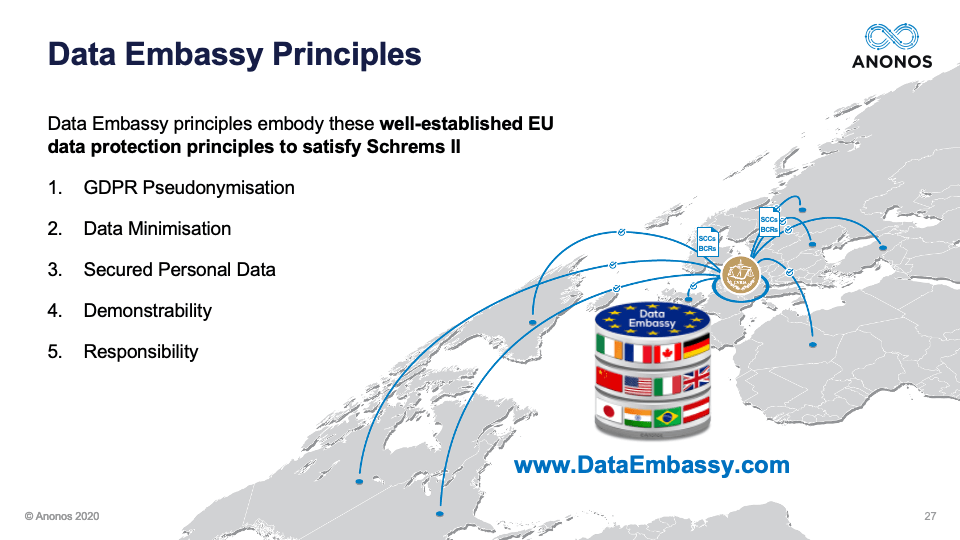
So, it has been referred to a couple of times. Maggie and I submitted a proposal to the European Data Protection Board. It is vendor-neutral. It is technology-neutral. It’s called Data Embassy. It embraces well-established EU data principles of GDPR Pseudonymisation, data minimisation, and securing the personal data. If you look closely to Articles 11(2) and 12(2), even within the GDPR for data subjects even within EU, it provides that if you can prove and this goes to Patrick’s suggestion that the data controller or the data processor is not themselves in possession of the keys necessary to relink, they are held to a lesser standard. And then, the ability to show that you’ve demonstrably complied with your obligations and you are standing up to your responsibility. So, this is a vendor-neutral, technology-neutral approach that embraces established EU principles and what we asked the EDPB was to tell us whether or not if people embrace these principles they would in fact be in compliance.

So, the last poll that we'd like to take of the audience is: Would you like the EDBP to include Data Embassy principles within their guidance? Yes or No.
So, again, the reason for this, as we're all seeking for clarity, the Data Embassy principles are predicated upon well-established EU principles, and the idea is if a data controller can show that they have satisfied that they should have the means to then have international data transfer, which is as we've discussed includes use of cloud providers, SaaS providers, outsource solutions. Yes, from the US but also from any other country. Any other country that does not have an adequacy decision. And when you look at some of the countries that have not received an adequacy decision, you are actually talking about the vast majority of providers. So, the idea here is the EDPB commenting on these Data Embassy Principles, which are well-established EU principles of Data Protection Law, vendor-neutral, technology neutral. Would it be helpful to provide you clarity and guidance so that you know that you are in a defensible business position because that clearly is what the vast majority of the audience on this webinar are shooting for.
So, we should have the results very shortly.
By the way, I may have misspoke myself. The EDPS published during this webinar clarification on what EU institutions have to do. It’s not the EDPB. Sorry, if I misspoke myself. I am getting notes from my fellow panelists that I messed up. So, we have not had EDPB Guidance but we have had EDPS Guidance. And so, this is a really an opportunity for us as a community to keep the education going and to continue this.
So, with that, do we have a result with no drums on this questionnaire? I will wait just a second more.
Okay. Fantastic. So, there’s a very strong need for clarity on this. 95% of the audience is saying it would be good to hear from the EDPB whether or not this Data Embassy Principle approach and concept would be helpful. Again, I think everyone is looking for clarity and we all need to be in a position where we can provide that and be in a position where we think we can move forward and we can conduct business in a way that enables us to do it in a way that's not subject us to liability.
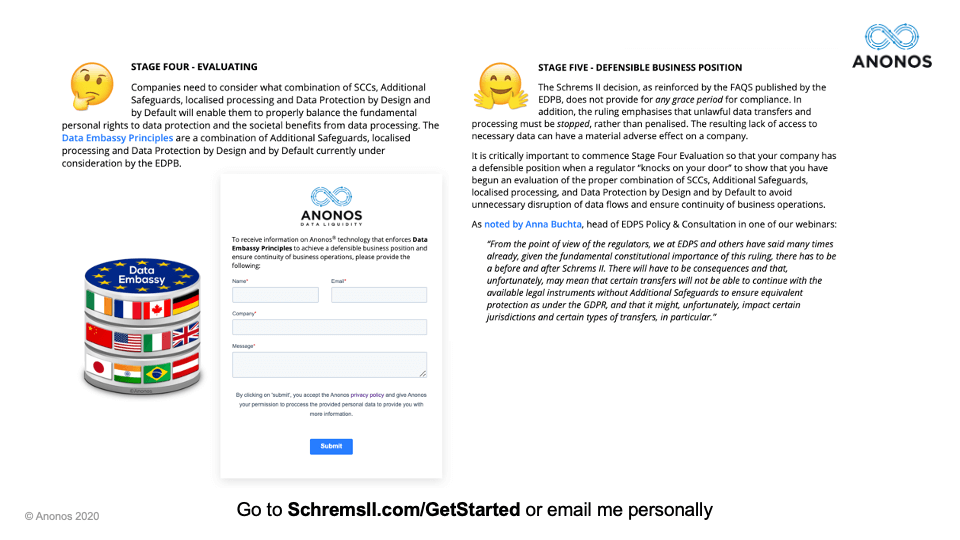
Just very quickly as we close. If you go to
www.SchremsII.com/GetStarted, it states through and walks through the different five stages. And for those of you who may be interested in learning information from Anonos and how we could help you comply both with the Data Embassy Principles but more importantly the Schrems II requirements, there is the opportunity there to fill in the field.
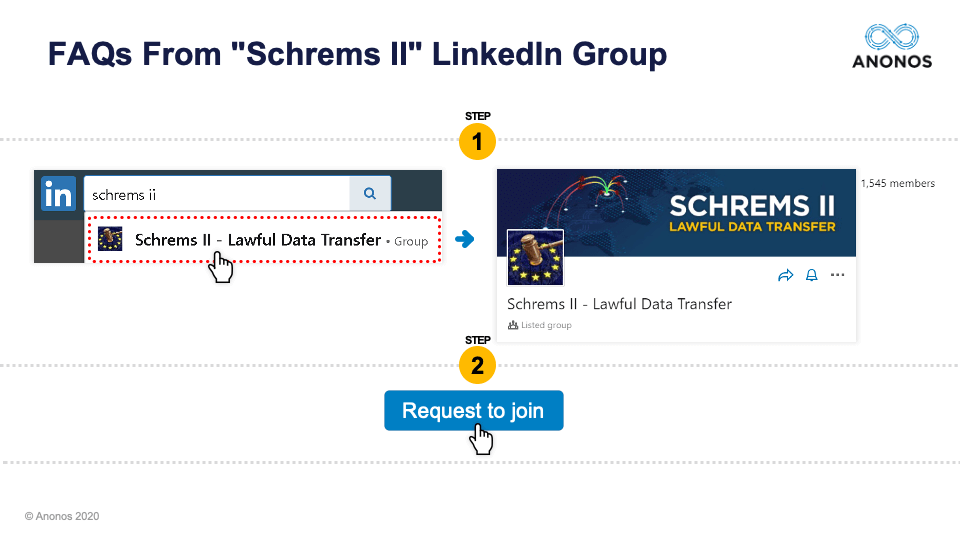
But most importantly, the community that we've developed through these two webinars is very robust. It’s senior. It’s willing and desiring to enforce and respect the fundamental rights of data subjects while accomplishing business goals. So, this is about a data stewardship mindset. And so, we would request for you to join or please link out to any of the panelists here on LinkedIn. I think any of the panelists and myself included would be happy to talk to you on a one-on-one basis.
And lastly, we will send out to everyone who registered by Wednesday of next week, a summary of the webinar and key takeaways together with the transcript and video. And in summary, I just want to thank the panelists. Thank you very much for your time. Additional safeguards do exist. Greater clarity will come in time, but they do exist today. And all of the companies represented on this webinar can in fact achieve a defensible business position while further clarity comes over time. Thank you very much everybody for your time. We appreciate it. Take care. Bye.
 Gabriela Zanfir
Gabriela Zanfir
 Patrick Van Eecke
Patrick Van Eecke
 John Bowman
John Bowman
 Mark Webber
Mark Webber
 Magali Feys
Magali Feys
 Gary LaFever
Gary LaFever
 Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator [00:00] Good morning and good afternoon. We welcome you to our second in a series of expert panel discussions about Schrems II additional safeguards. My name is Gary LaFever and I'm the General Counsel and CEO of Anonos, a global technology company specialising in GDPR-compliant Pseudonymisation and Data Protection by Design and by Default Technology and I will be serving as your moderator for today's event.
[00:00] Good morning and good afternoon. We welcome you to our second in a series of expert panel discussions about Schrems II additional safeguards. My name is Gary LaFever and I'm the General Counsel and CEO of Anonos, a global technology company specialising in GDPR-compliant Pseudonymisation and Data Protection by Design and by Default Technology and I will be serving as your moderator for today's event.  The first panel actually focused and included NOYB’s Romain Robert as well as the EDPS’ (European Data Protection Supervisor) Anna Buchta. And due to scheduling conflicts, neither Romain or Anna were able to attend but there are a few people who could replace both of them and one of Gabriela. So, we are very happy to have Gabriela with us today.
The first panel actually focused and included NOYB’s Romain Robert as well as the EDPS’ (European Data Protection Supervisor) Anna Buchta. And due to scheduling conflicts, neither Romain or Anna were able to attend but there are a few people who could replace both of them and one of Gabriela. So, we are very happy to have Gabriela with us today.  What I'd like to do very briefly since they are unable to join us is just highlight two quotes - one from Anna and one from Romain - from the last webinar. And the first one from Anna is that people should not fall into the trap, that the goal of additional safeguards and SCCs is to allow all the transfers that occurred prior to Schrems II. In fact, the truth of the matter is the fundamental rights that were the subject of Schrems II actually do require us to approach business differently and that is the healthy approach to doing it. But again, not at the cost of business, but rather business done correctly in compliance with and respecting and enforcing the fundamental rights of individuals. So, again, the goal of this webinar is to provide clarity on how you can continue your operations.
What I'd like to do very briefly since they are unable to join us is just highlight two quotes - one from Anna and one from Romain - from the last webinar. And the first one from Anna is that people should not fall into the trap, that the goal of additional safeguards and SCCs is to allow all the transfers that occurred prior to Schrems II. In fact, the truth of the matter is the fundamental rights that were the subject of Schrems II actually do require us to approach business differently and that is the healthy approach to doing it. But again, not at the cost of business, but rather business done correctly in compliance with and respecting and enforcing the fundamental rights of individuals. So, again, the goal of this webinar is to provide clarity on how you can continue your operations.  And from Romain, he pointed out that the three potential additional safeguards we will discuss today, which were initially raised by a German Data Protection Authority and have since been reiterated by both the EDPB and the EDPS. Romain brought the issue up that they are really not additional safeguards and that in fact you should be doing those already. Those three are encryption, Pseudonymisation, and anonymisation. And so, one of Romain’s points was if you are doing what you should be doing already correctly, it is less of a data transfer issue and more of an issue of “Are you within compliance?”
And from Romain, he pointed out that the three potential additional safeguards we will discuss today, which were initially raised by a German Data Protection Authority and have since been reiterated by both the EDPB and the EDPS. Romain brought the issue up that they are really not additional safeguards and that in fact you should be doing those already. Those three are encryption, Pseudonymisation, and anonymisation. And so, one of Romain’s points was if you are doing what you should be doing already correctly, it is less of a data transfer issue and more of an issue of “Are you within compliance?”  And I bring to your attention if you're not already aware that just last week, the EDPB finalised their opinion on Data Protection by Design and by Default. Data Protection by Design and by Default is just that by default you should be using just the minimally identifying data.
And I bring to your attention if you're not already aware that just last week, the EDPB finalised their opinion on Data Protection by Design and by Default. Data Protection by Design and by Default is just that by default you should be using just the minimally identifying data.  With that, I would like to provide each of the panelists an opportunity to introduce themselves. Gabriela, if you would please go first.
With that, I would like to provide each of the panelists an opportunity to introduce themselves. Gabriela, if you would please go first. Gabriela Zanfir-Fortuna (Future of Privacy Forum)
Gabriela Zanfir-Fortuna (Future of Privacy Forum) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Patrick Van Eecke (Cooley)
Patrick Van Eecke (Cooley) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator John Bowman (Promontory)
John Bowman (Promontory) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Magali Feys (Anonos)
Magali Feys (Anonos) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator What I'd like to do is to walk through what we've created, which are the 5 Stages of Additional Safeguards under Schrems II. And yes, the graphics are meant to be a little comical, but it's because it's a very serious point and what we've done is we've gone through the questions, the comments, the interactions, and the phone calls that we've had with actual participants in the first and this webinar to create these. And these are available at www.SchremsII.com/GetStarted. Before we actually start with a panelist perspective, we want to go into what we hear from you. I’m sorry. I forgot. Mark?
What I'd like to do is to walk through what we've created, which are the 5 Stages of Additional Safeguards under Schrems II. And yes, the graphics are meant to be a little comical, but it's because it's a very serious point and what we've done is we've gone through the questions, the comments, the interactions, and the phone calls that we've had with actual participants in the first and this webinar to create these. And these are available at www.SchremsII.com/GetStarted. Before we actually start with a panelist perspective, we want to go into what we hear from you. I’m sorry. I forgot. Mark? Mark Webber (Fieldfisher)
Mark Webber (Fieldfisher) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator The first is Awareness. There is a stage before Awareness. It's called Denial. But if you were in the Denial stage, you wouldn't be on this webinar. So, for those of you on this webinar, you obviously are clearly aware of the ruling in July, and I think what we've heard from quite a few of you is initially you thought that the geographic location of the servers would be controlling and I think that's one of the things that has evolved and has been a little surprising to some, which is who owns the servers and not where they're located. And so, that’s the first stage - Awareness.
The first is Awareness. There is a stage before Awareness. It's called Denial. But if you were in the Denial stage, you wouldn't be on this webinar. So, for those of you on this webinar, you obviously are clearly aware of the ruling in July, and I think what we've heard from quite a few of you is initially you thought that the geographic location of the servers would be controlling and I think that's one of the things that has evolved and has been a little surprising to some, which is who owns the servers and not where they're located. And so, that’s the first stage - Awareness.  The second stage is Acceptance. And by Acceptance here, what we're hearing from a lot of different people is that there are different stages of maturity and understanding, but there have been a few additional measures noted. And so, as to those measures, how could they help? We spent a lot of time in the first webinar and we'll speak again about Data Protection by Design and by Default. And as I noted, just last week, the European Data Protection Board passed the final version of their guidance on Data Protection by Design and by Default. And so, the reality is you're supposed to be having certain safeguards in place, regardless of whether the data is being processed within the EU, outside of the EU, or in the EU but by companies owned by US or other nation companies. And so, that's Acceptance, which is: “Okay. The Privacy Shield is gone. I've made a decision that the standard contractual clause is the way I want to go. Now, what do I do with regard to additional measures and additional safeguards?”
The second stage is Acceptance. And by Acceptance here, what we're hearing from a lot of different people is that there are different stages of maturity and understanding, but there have been a few additional measures noted. And so, as to those measures, how could they help? We spent a lot of time in the first webinar and we'll speak again about Data Protection by Design and by Default. And as I noted, just last week, the European Data Protection Board passed the final version of their guidance on Data Protection by Design and by Default. And so, the reality is you're supposed to be having certain safeguards in place, regardless of whether the data is being processed within the EU, outside of the EU, or in the EU but by companies owned by US or other nation companies. And so, that's Acceptance, which is: “Okay. The Privacy Shield is gone. I've made a decision that the standard contractual clause is the way I want to go. Now, what do I do with regard to additional measures and additional safeguards?”  Number three, at least again as we're looking through the interaction with the audience, is Understanding that at least at this point there are three that have been identified. No one of these will be a silver bullet, or a golden shield, or a magic wand. It will probably be a combination of these three and others that may develop over time. But these are the three that have been identified to date. And so, last webinar, we talked about the strengths and weaknesses of each of these. And I think what everyone came away with is it's likely a combination of the three that will work best and we'll touch upon the one which is Pseudonymisation in further detail because it's one of the FAQs that we're going to touch about. But this is not Pseudonymisation as defined prior to the GDPR. It's actually a heightened version with more stringent requirements. So, that's the third stage.
Number three, at least again as we're looking through the interaction with the audience, is Understanding that at least at this point there are three that have been identified. No one of these will be a silver bullet, or a golden shield, or a magic wand. It will probably be a combination of these three and others that may develop over time. But these are the three that have been identified to date. And so, last webinar, we talked about the strengths and weaknesses of each of these. And I think what everyone came away with is it's likely a combination of the three that will work best and we'll touch upon the one which is Pseudonymisation in further detail because it's one of the FAQs that we're going to touch about. But this is not Pseudonymisation as defined prior to the GDPR. It's actually a heightened version with more stringent requirements. So, that's the third stage.  The fourth stage is the evaluation stage - looking at what your business objectives are, realising that some of what you did in the past will have to be localised and then other operations will have to be enabled by Data Protection by Design and By Default. How do you do all those things in a way that allows you to achieve your business goals?
The fourth stage is the evaluation stage - looking at what your business objectives are, realising that some of what you did in the past will have to be localised and then other operations will have to be enabled by Data Protection by Design and By Default. How do you do all those things in a way that allows you to achieve your business goals?  And then, ultimately, I think everyone on this webinar is looking for that defensible business position. As noted by Anna Buchta in our prior webinar, this does not mean you do everything the way you did before without changes. Rather, you try to implement the minimal changes with the maximum benefit, respecting and enforcing the fundamental rights of EU data subjects while enabling you to achieve your business goals and objectives.
And then, ultimately, I think everyone on this webinar is looking for that defensible business position. As noted by Anna Buchta in our prior webinar, this does not mean you do everything the way you did before without changes. Rather, you try to implement the minimal changes with the maximum benefit, respecting and enforcing the fundamental rights of EU data subjects while enabling you to achieve your business goals and objectives.  So, those are the five different positions. What we'd like to do now is to hear in real time from this audience as to where do you want your organisation to be. And I want to make a technical comment here, for those of you who are using a web browser, as opposed to the Zoom software on your computer, if you could please send just in the subject heading 1, 2, 3, 4 or 5 to poll@SchremsII.com, we can count your vote as well. Right now, you should have on your screen those five options and we would love to see in real time where you would like your company to be - Awareness; Acceptance; Additional Safeguards - looking at what those are and learning about those; Evaluating those different options; or Do you want to be in a position where you have a Defensible Business Position?
So, those are the five different positions. What we'd like to do now is to hear in real time from this audience as to where do you want your organisation to be. And I want to make a technical comment here, for those of you who are using a web browser, as opposed to the Zoom software on your computer, if you could please send just in the subject heading 1, 2, 3, 4 or 5 to poll@SchremsII.com, we can count your vote as well. Right now, you should have on your screen those five options and we would love to see in real time where you would like your company to be - Awareness; Acceptance; Additional Safeguards - looking at what those are and learning about those; Evaluating those different options; or Do you want to be in a position where you have a Defensible Business Position?  Alright, so fascinating here. This is where people want their company to be - Evaluating Options 30%, and Defensible Business Position 52%. So, I think that's very helpful and provides for the panelists a sense of where you are at. In that way, we are able to customise our presentations just a little bit and make it so that it's something that even makes more relevance to all those in the audience.
Alright, so fascinating here. This is where people want their company to be - Evaluating Options 30%, and Defensible Business Position 52%. So, I think that's very helpful and provides for the panelists a sense of where you are at. In that way, we are able to customise our presentations just a little bit and make it so that it's something that even makes more relevance to all those in the audience.  By the way, the way that this is going to be structured is we took the top five Frequently Asked Questions from the first webinar, and we will be answering those top five FAQs. But we are going to reorder them based on the interest level and questions that were raised by today's audience. But I'd like to ask everyone to do a favor right now before we do that. If you are on your browser, go to LinkedIn and search for “Schrems II - Lawful Data Transfer” and you will see the LinkedIn Group where you can read these five FAQs. I’m going to provide a very high-level overview of what those FAQs say, but this is where you can get the full text of those FAQs.
By the way, the way that this is going to be structured is we took the top five Frequently Asked Questions from the first webinar, and we will be answering those top five FAQs. But we are going to reorder them based on the interest level and questions that were raised by today's audience. But I'd like to ask everyone to do a favor right now before we do that. If you are on your browser, go to LinkedIn and search for “Schrems II - Lawful Data Transfer” and you will see the LinkedIn Group where you can read these five FAQs. I’m going to provide a very high-level overview of what those FAQs say, but this is where you can get the full text of those FAQs.  Alright, so we're going to move on to the five FAQs. And these are the five FAQs that we will be talking about today. Again, I will reorder them slightly and you can reach and review the original FAQs and the answers that were prepared by a group of lawyers, data scientists, and business people. But I do want to say that Maggie was a co-author, but the other panelists were not authors of these FAQs. So, we're inviting them to agree, disagree, embellish, etc.
Alright, so we're going to move on to the five FAQs. And these are the five FAQs that we will be talking about today. Again, I will reorder them slightly and you can reach and review the original FAQs and the answers that were prepared by a group of lawyers, data scientists, and business people. But I do want to say that Maggie was a co-author, but the other panelists were not authors of these FAQs. So, we're inviting them to agree, disagree, embellish, etc.  Let’s proceed. The first one that we are going to address was actually the second Frequently Asked Question but it is by far the most often asked question in connection with this webinar - Do Boards of Directors and Stockholders need to be made aware of Schrems II? What about financial auditors and vertical industry regulators?
Let’s proceed. The first one that we are going to address was actually the second Frequently Asked Question but it is by far the most often asked question in connection with this webinar - Do Boards of Directors and Stockholders need to be made aware of Schrems II? What about financial auditors and vertical industry regulators?  Mark Webber (Fieldfisher)
Mark Webber (Fieldfisher) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Patrick Van Eecke (Cooley)
Patrick Van Eecke (Cooley) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Gabriela Zanfir-Fortuna (Future of Privacy Forum)
Gabriela Zanfir-Fortuna (Future of Privacy Forum) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Magali Feys (Anonos)
Magali Feys (Anonos) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator John Bowman (Promontory)
John Bowman (Promontory) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator [44:10] And John, what I'd like to do is use that to actually segue to the next question. The Board of Director question barely beat out this one. This is one that a lot of people have asked. In fact, I'm going to combine several questions that were asked to put it nicely (and some of the questions were not put quite this nicely) that either the US big tech companies have not read the ruling and understood or they are purposely misleading their customers. These were some very pointed questions and statements that we have SCCs in place is only half the question because under the GDPR, it's a data controller obligation. It's not a data processor obligation. It's not a vendor obligation. And so, it's not that I'm defending anyone. But the reality is, my own personal view and obviously the panelists will disagree with me if they don't hold it is that it is imprudent for a data controller to expect any company to satisfy their obligations when under the GDPR they're clearly set forth as one of the data controllers.
[44:10] And John, what I'd like to do is use that to actually segue to the next question. The Board of Director question barely beat out this one. This is one that a lot of people have asked. In fact, I'm going to combine several questions that were asked to put it nicely (and some of the questions were not put quite this nicely) that either the US big tech companies have not read the ruling and understood or they are purposely misleading their customers. These were some very pointed questions and statements that we have SCCs in place is only half the question because under the GDPR, it's a data controller obligation. It's not a data processor obligation. It's not a vendor obligation. And so, it's not that I'm defending anyone. But the reality is, my own personal view and obviously the panelists will disagree with me if they don't hold it is that it is imprudent for a data controller to expect any company to satisfy their obligations when under the GDPR they're clearly set forth as one of the data controllers.  John Bowman (Promontory)
John Bowman (Promontory) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Gabriela Zanfir-Fortuna (Future of Privacy Forum)
Gabriela Zanfir-Fortuna (Future of Privacy Forum) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Magali Feys (Anonos)
Magali Feys (Anonos) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Mark Webber (Fieldfisher)
Mark Webber (Fieldfisher) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator So, with that, we're going to go to the next question. And this, we touched upon at length in the prior webinar and I don't think it's as much of a question as it was initially. And in fact, the EDPB was very clear in the FAQs. In fact, BCRs are similar to SCCs. So, I think hopefully we can make a quick coverage of this.
So, with that, we're going to go to the next question. And this, we touched upon at length in the prior webinar and I don't think it's as much of a question as it was initially. And in fact, the EDPB was very clear in the FAQs. In fact, BCRs are similar to SCCs. So, I think hopefully we can make a quick coverage of this.  But I do want to mention again last week that the EDPB had mentioned that and ratified that Data Protection by Design by Default is not optional. It's mandatory. And at least working with our clients, those that are engaged in Data Protection by Design and By Default, complying with Schrems II is a lot easier, which is another way of saying perhaps the reason a lot of companies have issues with Schrems II is because they weren't already doing Data Protection by Design and by Default. So, if we could kind of pick up the response a little bit here. Patrick, if you would please go first. Thank you.
But I do want to mention again last week that the EDPB had mentioned that and ratified that Data Protection by Design by Default is not optional. It's mandatory. And at least working with our clients, those that are engaged in Data Protection by Design and By Default, complying with Schrems II is a lot easier, which is another way of saying perhaps the reason a lot of companies have issues with Schrems II is because they weren't already doing Data Protection by Design and by Default. So, if we could kind of pick up the response a little bit here. Patrick, if you would please go first. Thank you. Patrick Van Eecke (Cooley)
Patrick Van Eecke (Cooley) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator So, in order to ensure that we can finish, I am going to move on to the next FAQ. And the reason this is highly relevant is that many people will cite an EU employee processing as an example of something that simply is impossible to do in compliance with Schrems II. The FAQ, which I won't go into a lot of detail, although it's a very detailed response, actually provides three different examples of how data could be processed by implementing and embracing Data Protection by Design and by Default. In fact, our experience, as I've said in the past, is companies that are following Data Protection by Design and by Default methodology have a much easier time of complying with Schrems II. So, again, we will use this question, but I would please ask each of the panelists to keep their responses to 30 seconds so we can complete it all. So, Mark, if you would please start.
So, in order to ensure that we can finish, I am going to move on to the next FAQ. And the reason this is highly relevant is that many people will cite an EU employee processing as an example of something that simply is impossible to do in compliance with Schrems II. The FAQ, which I won't go into a lot of detail, although it's a very detailed response, actually provides three different examples of how data could be processed by implementing and embracing Data Protection by Design and by Default. In fact, our experience, as I've said in the past, is companies that are following Data Protection by Design and by Default methodology have a much easier time of complying with Schrems II. So, again, we will use this question, but I would please ask each of the panelists to keep their responses to 30 seconds so we can complete it all. So, Mark, if you would please start. Mark Webber (Fieldfisher)
Mark Webber (Fieldfisher) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator John Bowman (Promontory)
John Bowman (Promontory) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Magali Feys (Anonos)
Magali Feys (Anonos) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Gabriela Zanfir-Fortuna (Future of Privacy Forum)
Gabriela Zanfir-Fortuna (Future of Privacy Forum) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Well, I think that enables us to then move on to the next question and that has to do with Pseudonymisation. Again, we touched upon this at great length in the prior webinar, but the only guidance out there so far is from regional DPAs and they have mentioned encryption, Pseudonymization, and anonymisation. And so, I encourage anyone who is participating in this webinar and did not see the first one, I'm happy to give you a link. We have a summary, we have a transcript, we have the video. But briefly though, I'd just like to summarize that Pseudonymisation (and this is something quite candidly I've learned in the last few months) - you have to be careful with this term. There were actually efforts during the drafting of the GDPR to introduce Pseudonymisation as a third category. So, you have personal data, non-personal data, and Pseudonymisation.
Well, I think that enables us to then move on to the next question and that has to do with Pseudonymisation. Again, we touched upon this at great length in the prior webinar, but the only guidance out there so far is from regional DPAs and they have mentioned encryption, Pseudonymization, and anonymisation. And so, I encourage anyone who is participating in this webinar and did not see the first one, I'm happy to give you a link. We have a summary, we have a transcript, we have the video. But briefly though, I'd just like to summarize that Pseudonymisation (and this is something quite candidly I've learned in the last few months) - you have to be careful with this term. There were actually efforts during the drafting of the GDPR to introduce Pseudonymisation as a third category. So, you have personal data, non-personal data, and Pseudonymisation.  And one of the reasons I at least believe it's very important is because almost by definition, the Article 4(5) definition of Pseudonymisation literally says: “You must, on a result basis, be able to put controls in place so that an EU data exporter is the only one who can relink to identity.” And if in fact that that's been done, if the EU data exporter is the only one that holds the keys and the data is being processed by a non-EU importer, again, if you have in fact satisfied the definition of requirements, you should be in compliance with Schrems II. But with that, I'd like to start off and get the panelists’ perspective. Maggie, if you would, please.
And one of the reasons I at least believe it's very important is because almost by definition, the Article 4(5) definition of Pseudonymisation literally says: “You must, on a result basis, be able to put controls in place so that an EU data exporter is the only one who can relink to identity.” And if in fact that that's been done, if the EU data exporter is the only one that holds the keys and the data is being processed by a non-EU importer, again, if you have in fact satisfied the definition of requirements, you should be in compliance with Schrems II. But with that, I'd like to start off and get the panelists’ perspective. Maggie, if you would, please. Magali Feys (Anonos)
Magali Feys (Anonos) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Mark Webber (Fieldfisher)
Mark Webber (Fieldfisher) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator John Bowman (Promontory)
John Bowman (Promontory) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Patrick Van Eecke (Cooley)
Patrick Van Eecke (Cooley) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator Gabriela Zanfir-Fortuna (Future of Privacy Forum)
Gabriela Zanfir-Fortuna (Future of Privacy Forum) Gary LaFever (Anonos) - Moderator
Gary LaFever (Anonos) - Moderator So, what we'd like to do at this point in time is we'd actually like to re-poll the audience. Having listened to this discussion by the panelists, previously 82% of the audience wanted to be in stage four or five - Evaluating Options or Defensible Business Positions. You've heard a lot of things said that some of these things will not be resolved perhaps for years. Yet, at the same time, it’s an issue of potential risk that needs to be raised to the C-Suite, to the CEO, and to the Board. And so, just curious and we will now take the poll as to whether or not people’s attitudes have changed. And so, we are asking you where you would like to be in these five positions - just awareness, acceptance, additional safeguards where you are aware of what at least has been discussed today, evaluating your different options, or in a position where you actually have a defensible business position. So, if you would please go forward with that. As I’ve said in the past, if you are using a web-based browser, you can send in the subject heading 1, 2, 3, 4, or 5 to poll@schremsII.com and we will share that with you.
So, what we'd like to do at this point in time is we'd actually like to re-poll the audience. Having listened to this discussion by the panelists, previously 82% of the audience wanted to be in stage four or five - Evaluating Options or Defensible Business Positions. You've heard a lot of things said that some of these things will not be resolved perhaps for years. Yet, at the same time, it’s an issue of potential risk that needs to be raised to the C-Suite, to the CEO, and to the Board. And so, just curious and we will now take the poll as to whether or not people’s attitudes have changed. And so, we are asking you where you would like to be in these five positions - just awareness, acceptance, additional safeguards where you are aware of what at least has been discussed today, evaluating your different options, or in a position where you actually have a defensible business position. So, if you would please go forward with that. As I’ve said in the past, if you are using a web-based browser, you can send in the subject heading 1, 2, 3, 4, or 5 to poll@schremsII.com and we will share that with you.  And as they're displayed. So, we are at 90%. So, it looks like a slightly larger percentage now want to actually ensure that they are in a defensible business position or evaluating options. And it is interesting. I always find it interesting to watch what EU member states do. So, if you look, the UK has announced revisiting their cloud-first strategy. In France, the CNIL actually went so far as to say that the data hub should be pulled out of Azure. But then, another French Court came in and said that may be the appropriate resolution but let’s look at this in a guided and guarded manner. And so, the EU member states are telegraphing the importance of this issue and one that needs to be resolved and that’s why just waiting is not really an option and rather taking position and actions are what is required but in a reasonable way as we’ve talked through during this.
And as they're displayed. So, we are at 90%. So, it looks like a slightly larger percentage now want to actually ensure that they are in a defensible business position or evaluating options. And it is interesting. I always find it interesting to watch what EU member states do. So, if you look, the UK has announced revisiting their cloud-first strategy. In France, the CNIL actually went so far as to say that the data hub should be pulled out of Azure. But then, another French Court came in and said that may be the appropriate resolution but let’s look at this in a guided and guarded manner. And so, the EU member states are telegraphing the importance of this issue and one that needs to be resolved and that’s why just waiting is not really an option and rather taking position and actions are what is required but in a reasonable way as we’ve talked through during this.  So, if I can summarise very quickly at least what I believe has been discussed today. First, Schrems II is in fact a Board/CEO level issue but it needs to work its way through the appropriate safeguards and structures and communications, but it is something that could have an impact and therefore needs to be considered. You really can’t expect cloud, SaaS, or outsource providers to provide you guidance to solve the problem. It’s a contractual issue and you should look at the contracts that you have in place regarding who is responsible for what. SCCs and BCRs both work, and Patrick made a very good case for BCRs that may work in more situations than they’re even currently being used for, but they are only contracts and one of the holdings of the Schrems II decision was in fact that contracts by themselves may not be enough. And when you are transferring to a country that does not have equivalent protection, you will need something more than just contracts.
So, if I can summarise very quickly at least what I believe has been discussed today. First, Schrems II is in fact a Board/CEO level issue but it needs to work its way through the appropriate safeguards and structures and communications, but it is something that could have an impact and therefore needs to be considered. You really can’t expect cloud, SaaS, or outsource providers to provide you guidance to solve the problem. It’s a contractual issue and you should look at the contracts that you have in place regarding who is responsible for what. SCCs and BCRs both work, and Patrick made a very good case for BCRs that may work in more situations than they’re even currently being used for, but they are only contracts and one of the holdings of the Schrems II decision was in fact that contracts by themselves may not be enough. And when you are transferring to a country that does not have equivalent protection, you will need something more than just contracts.  So, it has been referred to a couple of times. Maggie and I submitted a proposal to the European Data Protection Board. It is vendor-neutral. It is technology-neutral. It’s called Data Embassy. It embraces well-established EU data principles of GDPR Pseudonymisation, data minimisation, and securing the personal data. If you look closely to Articles 11(2) and 12(2), even within the GDPR for data subjects even within EU, it provides that if you can prove and this goes to Patrick’s suggestion that the data controller or the data processor is not themselves in possession of the keys necessary to relink, they are held to a lesser standard. And then, the ability to show that you’ve demonstrably complied with your obligations and you are standing up to your responsibility. So, this is a vendor-neutral, technology-neutral approach that embraces established EU principles and what we asked the EDPB was to tell us whether or not if people embrace these principles they would in fact be in compliance.
So, it has been referred to a couple of times. Maggie and I submitted a proposal to the European Data Protection Board. It is vendor-neutral. It is technology-neutral. It’s called Data Embassy. It embraces well-established EU data principles of GDPR Pseudonymisation, data minimisation, and securing the personal data. If you look closely to Articles 11(2) and 12(2), even within the GDPR for data subjects even within EU, it provides that if you can prove and this goes to Patrick’s suggestion that the data controller or the data processor is not themselves in possession of the keys necessary to relink, they are held to a lesser standard. And then, the ability to show that you’ve demonstrably complied with your obligations and you are standing up to your responsibility. So, this is a vendor-neutral, technology-neutral approach that embraces established EU principles and what we asked the EDPB was to tell us whether or not if people embrace these principles they would in fact be in compliance.  So, the last poll that we'd like to take of the audience is: Would you like the EDBP to include Data Embassy principles within their guidance? Yes or No.
So, the last poll that we'd like to take of the audience is: Would you like the EDBP to include Data Embassy principles within their guidance? Yes or No.  Okay. Fantastic. So, there’s a very strong need for clarity on this. 95% of the audience is saying it would be good to hear from the EDPB whether or not this Data Embassy Principle approach and concept would be helpful. Again, I think everyone is looking for clarity and we all need to be in a position where we can provide that and be in a position where we think we can move forward and we can conduct business in a way that enables us to do it in a way that's not subject us to liability.
Okay. Fantastic. So, there’s a very strong need for clarity on this. 95% of the audience is saying it would be good to hear from the EDPB whether or not this Data Embassy Principle approach and concept would be helpful. Again, I think everyone is looking for clarity and we all need to be in a position where we can provide that and be in a position where we think we can move forward and we can conduct business in a way that enables us to do it in a way that's not subject us to liability.  Just very quickly as we close. If you go to www.SchremsII.com/GetStarted, it states through and walks through the different five stages. And for those of you who may be interested in learning information from Anonos and how we could help you comply both with the Data Embassy Principles but more importantly the Schrems II requirements, there is the opportunity there to fill in the field.
Just very quickly as we close. If you go to www.SchremsII.com/GetStarted, it states through and walks through the different five stages. And for those of you who may be interested in learning information from Anonos and how we could help you comply both with the Data Embassy Principles but more importantly the Schrems II requirements, there is the opportunity there to fill in the field.  But most importantly, the community that we've developed through these two webinars is very robust. It’s senior. It’s willing and desiring to enforce and respect the fundamental rights of data subjects while accomplishing business goals. So, this is about a data stewardship mindset. And so, we would request for you to join or please link out to any of the panelists here on LinkedIn. I think any of the panelists and myself included would be happy to talk to you on a one-on-one basis.
But most importantly, the community that we've developed through these two webinars is very robust. It’s senior. It’s willing and desiring to enforce and respect the fundamental rights of data subjects while accomplishing business goals. So, this is about a data stewardship mindset. And so, we would request for you to join or please link out to any of the panelists here on LinkedIn. I think any of the panelists and myself included would be happy to talk to you on a one-on-one basis.  And lastly, we will send out to everyone who registered by Wednesday of next week, a summary of the webinar and key takeaways together with the transcript and video. And in summary, I just want to thank the panelists. Thank you very much for your time. Additional safeguards do exist. Greater clarity will come in time, but they do exist today. And all of the companies represented on this webinar can in fact achieve a defensible business position while further clarity comes over time. Thank you very much everybody for your time. We appreciate it. Take care. Bye.
And lastly, we will send out to everyone who registered by Wednesday of next week, a summary of the webinar and key takeaways together with the transcript and video. And in summary, I just want to thank the panelists. Thank you very much for your time. Additional safeguards do exist. Greater clarity will come in time, but they do exist today. And all of the companies represented on this webinar can in fact achieve a defensible business position while further clarity comes over time. Thank you very much everybody for your time. We appreciate it. Take care. Bye.